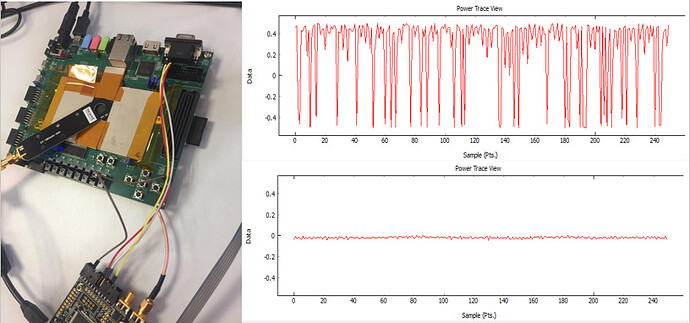
Hello,
I have recently implemented AES on my ZedBoard and made it comunicate with the Chipwhisperer lite but I noticed an irregularity in my system. When I take power traces with H-Probe sometimes there are wierd spikes in the traces:
The abnormal case is the upper one and the normal is below him.
A picture of our setup in added above.
Additional information :
The zedboard is powered by 12V.
In the 20 pin connector the pins that are connected are:
Pin2(GND) to ZedBoard ground
Pin10(TIO1) is TX
Pin12(TIO2) is RX
Pin16(TIO4) gets trigger from zedboard
Do you have an idea what can cause this irregularity?
@yonatan I’m more surprised by the absence of spikes in your normal plot; it’s a bit hard to tell from the scale, but that looks like a suprisingly clean trace for an EM probe.
For the abnormal case, could there be some EM interference from elsewhere?
Are you able to run an attack successfully?
Are you doing AES in HW or SW?
Jean-Pierre
Hi, I do the HW attack, I showed both cases in the same scale so that the irregularity can be seen clearly. I don’t believe that it is caused by EM interference because when I took measures on a table (which emits no EM) instead on the chip I got the same irregularity when the normal case showed little noise. I also know that my chipwhisperer kit works properly because I did the same measurements on CW308T-XMEGA and it worked
@yonatan do you mean that you occasionally observe the same noise spikes when you measure from a table? If so that suggests that there is some other EM source causing this noise.
HW AES is generally rather tiny, so it’s quite possible that its power trace gets drowned out by something else.
When you say that measurements on XMEGA worked, do you mean that you were able to attack the AES key? Or that you didn’t observe the noise spikes? If you get noise spikes from the “table”, you should get them no matter what target you use; have I misunderstood?
Jean-Pierre
Sorry for my unclear explanation. When I did the attack on XMEGA the irregularity didn’t occur. Furthermore, after ~200 traces most of the subkeys were found by the cpa algorithm. When I did the attack on my Zedboard, the irregularity occurred in random traces and the algorithm couldn’t find any subkeys. The irregularity occurred wether I took measurements from the board or a non-emiting EM table. I need to mention that the only differences between the systems are the 20 pin connector’s connections, the Zedboard is not powered supply by the chipwhisperer, and my system is HW designed and not SW designed. Both attacks were taken in the same environment. Thanks for your help,
Yonatan
A few thoughts: make sure your ground is well connected, and connect all 3 grounds on the 20-pin connector for extra insurance… that could be the cause right there.
And if you haven’t already, have a look at the HW AES tutorial. Notice that:
1- HW implementations require a lot more traces (around 3000 for the CW305 example);
2- you may need a different attack model.
In your case, using an EM probe means you’ll likely need even more traces (with or without the spikes). You didn’t mention how frequent the spikes are, but they shouldn’t prevent an attack from succeeding.
(Unfortunately the tutorial hasn’t been updated for CW4… however there is an example for CW5 in software/jupyter/PA_HW_CW305.ipynb.)
Jean-Pierre
1 Like