Sorry to bother you, jpthibault. I replaced sbox in TINYAES128C with a composite domain implementation, and then I used some DPA schemes provided by chipwhisker to attack, but found that it was not possible to successfully attack. Of course, it can run successfully in Recovering Data from a Single Bit. ipynb, but it cannot successfully recover a single character in DPA on Firmware Implementation of AES (Main). ipynb, and it cannot be successfully attacked in other DPA attacks. I also want to ask you, does chipWhisperer provide a more powerful DPA model that can carry out more powerful attacks?
In the future, can you start a separate topic for questions such as this one (since it has nothing to do with the original question)? This makes it easier for others to search and learn from previously answered forum questions.
ChipWhisperer comes with a bunch of basic models:
import chipwhisperer.analyzer as cwa
print(cwa.leakage_models)
If you go through all of the AES notebooks in our courses, you’ll come across a few different uses of the leakage models.
One of the reasons that the ChipWhisperer analyzer code is open source is to make it possible to extend: if there is no model suitable for your target, you can write your own.
If you re-frame your question with more details about the implementation that you are trying to attack (as a separate topic ![]() ), maybe other forum readers will have some advice.
), maybe other forum readers will have some advice.
It may also be worthwhile to check out other open-source side-channel attack frameworks:
hi jpthibault,I have installed version 4.0, but when I clicked on chipwhisperer capture, there was no response. I would like to inquire if there is a video of installing version 4.0, as I saw that the only one online was from 2015, which is too clich é. I chose version 4.0 because the current version is a bit uncomfortable to use
As mentioned above: we don’t support it.
hi jpthibault,
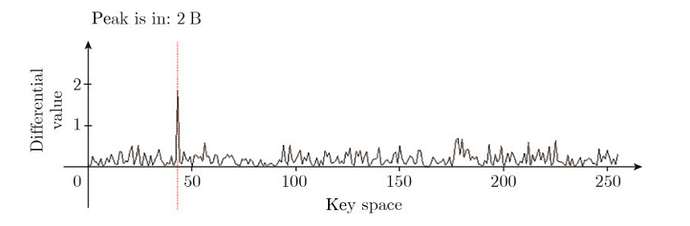
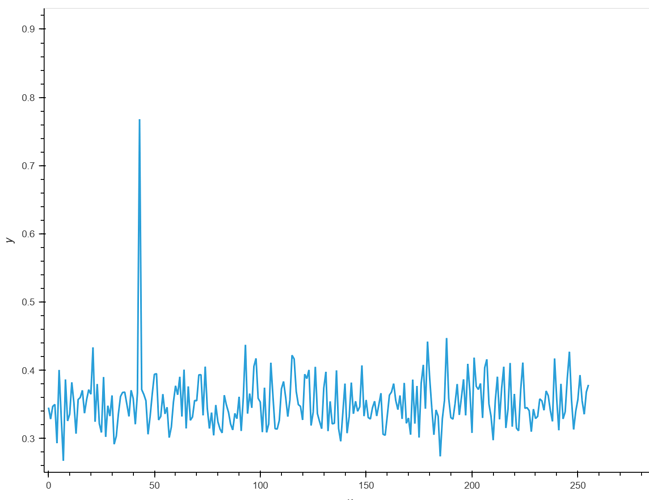
I would like to consult with you how to obtain this image when using Lab 4_2 - CPA on Firmware Implementation of AES (HARDWARE) .Or how to draw a line chart of the correlation coefficient (cpaoutput)?
hi jpthibault,I see you haven’t answered me for a long time,so there was no way to get above picture?
Do you mean just this?
cw.plot(maxcpa)
yes.through this method, I can obtain images. But how to change the names of the x-axis and y-axis of the image, the units of the previous x-axis and y-axis, just like the image above
cw.plot() is just a wrapper around holoviews. Have a look at the holoviews documentation.
Can you help me? I found out how to change the x-axis and y-axis names, but I don’t know how to change the y-axis scale
I couldn’t find it in the document you sent
from a quick google search: Customizing Plots — HoloViews v1.18.1
I’m sorry, I still couldn’t find it
I would like to ask you if in SubBytes, changing its output in some form can resist CPA attacks?
Does changing the instantaneous output have a significant impact on resisting CPA attacks?
Possibly, it depends how you do it. This is one of the principles of masking.