Hello everyone, I need to do some experience on the directory where has a masked implementation of AES, and I don’t what I need to put on jupyter to search on this directory. Just I need to do AVR compiler on this folder identify by ‘CRYPTO_TARGET’ or I need to do another thing.
This directory is /hardware/victims/firmware/crypto/secAES-ATmega8515
Hi,
You’ll first need to clone the secAES-ATmega8515 submodule (should be something along the lines of git submodule update --init secAES-ATmega8515). Once that’s done, you can compile by using the MASKEDAES crypto target. I’m not sure what microcontroller targets library will support.
Alex
Hi Alex, I’m using the target CW308 XMEGA for this tests, but i don’t know if I’d need API Atmel Interface for do the programming, because I just using the CW308 UFO Board and CWLite connected with this target and when I do this with MASKEDAES I’ve a problem with the trigger on target. What I need to do you think?
Looking at https://github.com/ANSSI-FR/secAES-ATmega8515/tree/master/src, I think you’ll need to load a binary into the EEPROM (there should be a .eep file as an output of the build process). The XMega programmer should support this, and I think the .eep file is the same format as the .hex, so things should just work there.
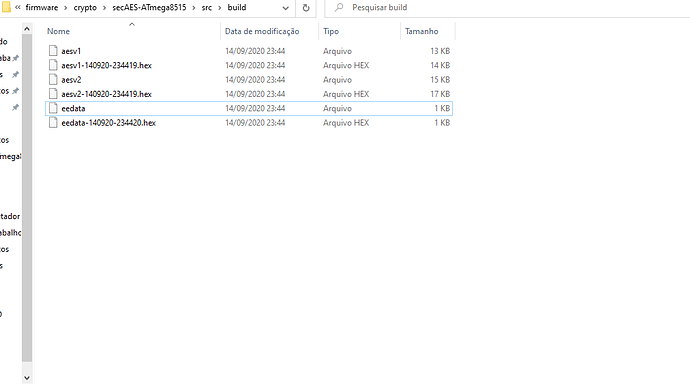
Hey Alex, but when I do the makefile the generate just .hex file for both AESv1 and AESv2, so have another .hex file from EEDATA. See on the picture below we’ve the .hex file. I have been tested for the both AES and has the same problem, failed for trigger out. Don’t I need it a ATmega Interface for communication with AVR to the board?
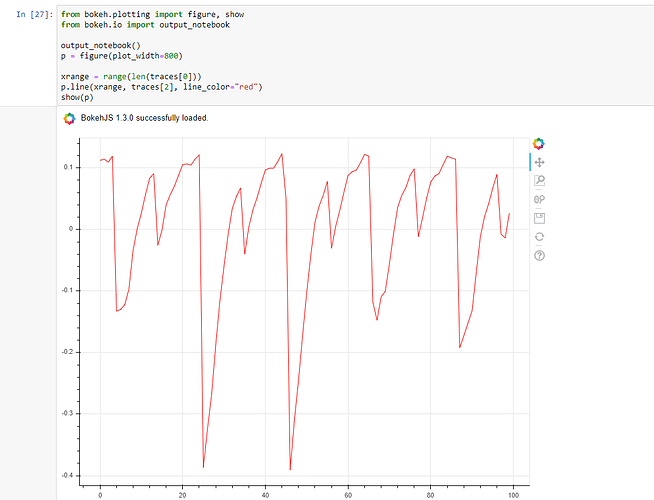
Hey Alex, I got it to test on CW308 and I’ve this characteristic from the analysis and capture from XMEGA. Now I try to attack utilizing CPA to saw what’s happen.
Thanks for report.
Where are the documentation from this type of secAES128, because on the directory just has one pdf describing for each one? Do you know something about this?
I found a paper using the repository here: https://www.n0secure.org/wp-content/uploads/2018/11/053.pdf
as well as associated slides here (I think): https://www.internet-of-everything.fr/wp-content/uploads/2018/05/EmmanuelProuff_ANSSI.pdf, so those might be worth a read.
Oh thanks for this support, I’ll read this because I study that method of encryptation for my research. Another point when I’ve doubt I serve this forum again.
Thanks