Hi, I need some advice on an analysis I am doing for my research. Disclosure: I don’t have much background in security. My research focuses on computer hardware. So any advice/suggestions you have for me would be much appreciated.
I am trying to carry out a power side channel analysis on the CW-NANO platform. I am trying to attack the modulus operation, which seems to be most typically implemented as a division to get the remainder. For the M0 CPU used in the CW-NANO, division is implemented in software. Looking at the assembly code, this operation is implemented as a sequence of shifts and subtracts.
In my case, the dividend a is known to the attacker already. So its just a matter of finding the divisor b to recover the remainder (i.e., r = a%b) . First, I did a test to see if the number of cycles required would vary based on the dividend (a) and the divisor (b). Here is a table of the time taken (in CPU cycles) for different combinations of a/b on the ARM-M0 CPU.
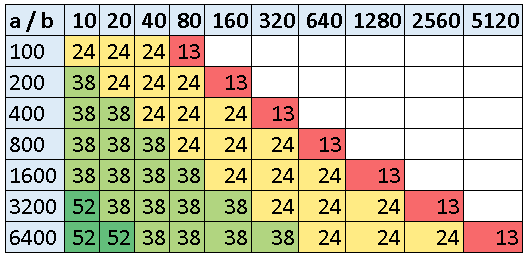
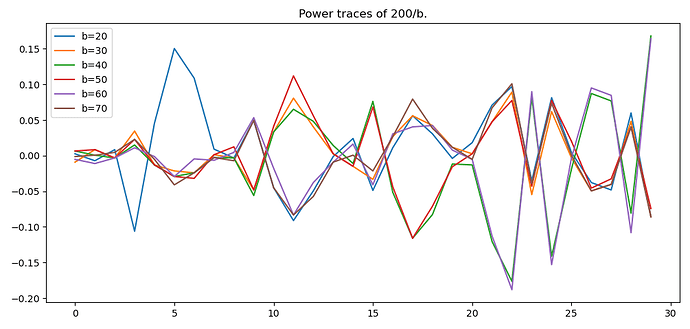
Its therefore pretty easy to establish the range of b based on the time taken for division. Next, I wanted to see, for the range of values which take the same amount of time, is the power trace different? So, I captured traces of 200/b and then subtracted the average of all traces and plotted them. Here is that graph:
To me, it seems like there are significant differences based on the value being used. A few caveats: 1) I plotted only powers of 10 for simplicity but ideally, I’d like this to work for all values of b and 2) I took 100 traces for each b value and they are all identical.
My question is: how should I go about ‘predicting’ the value of b given a trace? I’m not sure CPA is the right approach since there isn’t a single ‘peak’ similar to the Hamming weight. Would multi-variate CPA work? Or should I try to train some type of classification model to see if that can predict the value? Thank you!