Hi,
I’m trying to perform a template attack directly on the 16 sub-keys of the AES-128 ECB implementation on CW308 using CW Lite. My goal is to be able to guess the correct 16 key-bytes with just one attack plaintext. Here is the setup:
- For templates I collect 300 000 traces with random key and fixed plaintext (want to start with the easiest case first)
- For attack: fixed key (key: 0x00, 0x11, 0x22, …, 0xFF), and fixed plaintext (same as for the template making phase)
- For finding POIs, I use principal component analysis (PCA)
- I use the pooled covariance matrix for the attack, and just looking at the exponent of the distribution terms (so -0.5* …)
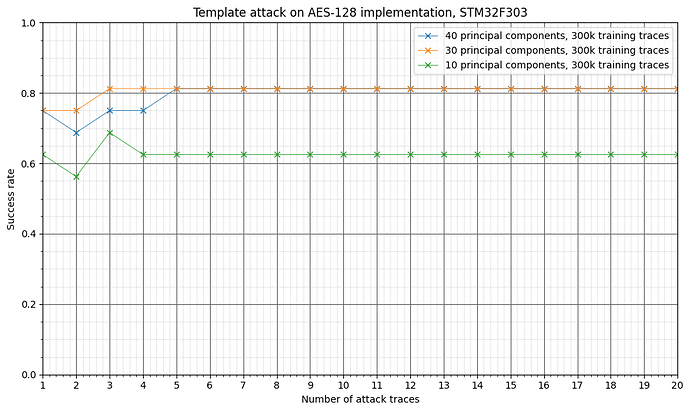
- For each number of attack traces, n, I define a success when the sub-key is correctly guessed using n traces in the attack (so a binary assignment of 0 or 1). And thus the success rate becomes the average sum of these 0s and 1s over the 16 different sub-keys
- I parametrize over the number of principal components I use to pick out the POIs
The following shows the results:
I understand why the plots flatten out in this case, cause with the fixed key and fixed plaintext, I guess you’re just integrating out the random noise, right? However, I’d like to see these success rates preferably at 1.
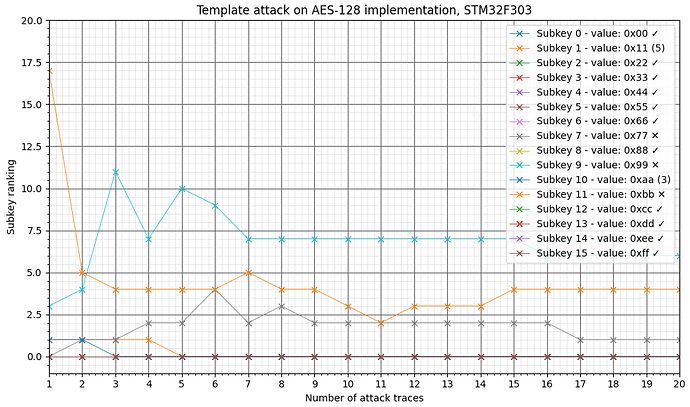
To give a more detailed view of the case when the number of principal components is 40, I’ve made this plot of the sub-key rankings as a function of number of attack traces:
In the legend, the positive checkmark indicates that the subkey was correctly guessed after just 1 attack trace. The number in parenthesis is the number of attack traces needed to get a rank 0 (and stays at rank 0 for the remaining of the 20 attack traces). The cross checkmark indicates that the sub-key does not have rank 0 after 20 attack traces. So this leads me to some questions:
- Do I need more training traces? Any idea how many I’d need ballpark wise? Just a reminder, these results are for the, supposedly, easiest case with fixed plaintext both in the training and attack phase. Just would like some input before I possibly waste a lot of time if there’s something else that might be the issue
- As for calculating the success rate, I assume there might be better and more established ways. Any ideas what I should use as a metric instead of how I’ve done it?
- Any suggestions for how to make the template attacks more successful?
Thanks for any input!