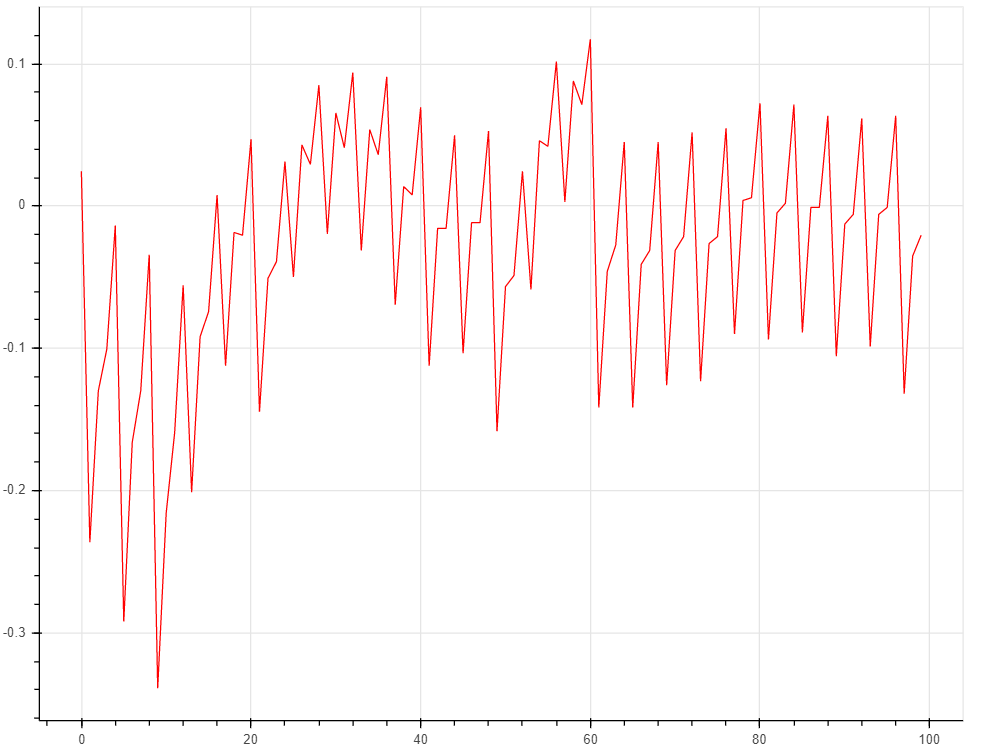
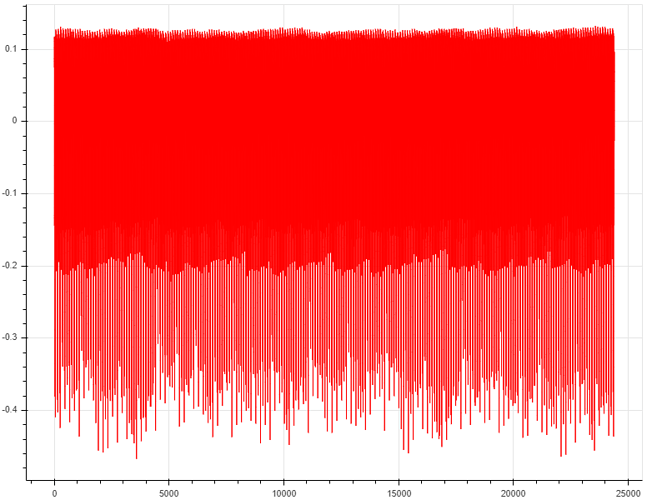
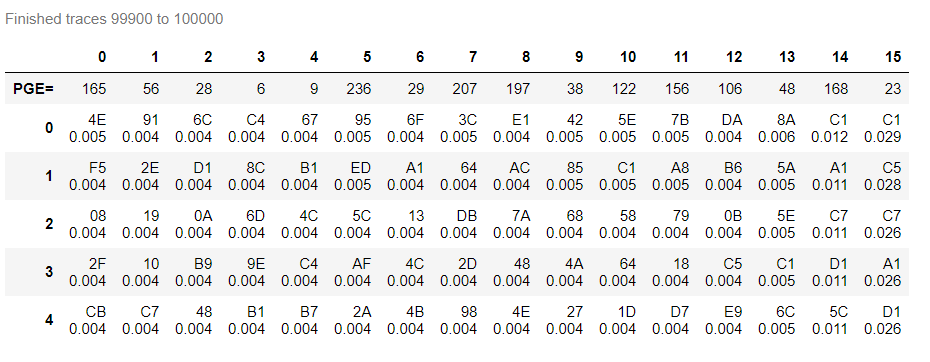Hello everyone, I need some help to break this type of implementation for AES utilizing a CPA attack. My target is the CW308 XMEGA, but I didn’t have some results what I want. I’m work with 100k of traces and I don’t have the key, so I need some help for do this.
This is the trace when I capture from my Chipwhisperer Lite connected on my CW308 UFO Board. That traces are for breaking the key for AES implementation on target XMEGA and compare with others implementation AES like secAES that has on chipwhisperer directory. I need to do this for compare the PGE vs Traces, but I never break de key with this numbers of traces.
Your traces are too short. Try capturing traces with a length of 5000 (scope.adc.samples = 5000)
50 traces is probably sufficient to break tinyaes
Ohh thanks and sorry for my stupid question hahahaha, I’m a beginner from this test and I learn too much with this forum.
Thank you so much
1 Like