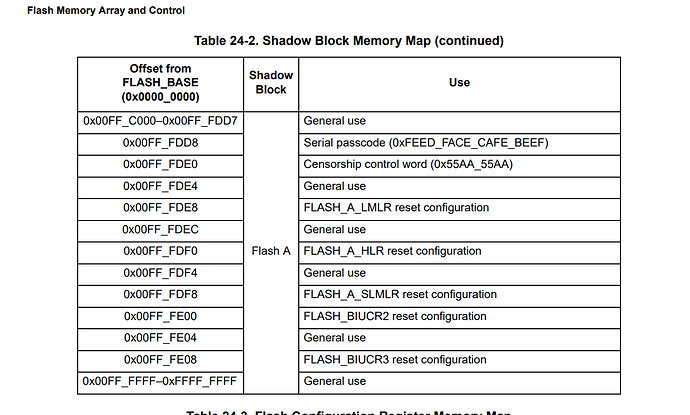
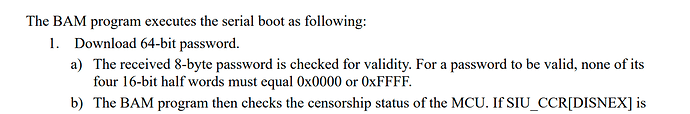
Hello I’m using the MPC5676R target board and wanted to set the flash password and censorship value. I could find any code in the GitHub repo that illustrated this, and the PEMicro debugging software only offers a uncensor option, but not a set password or censor option. Additionally, the MPC5676 doesn’t have an application note on how to implement this, so I reluctantly used the the application note for the MPC563x series (AN3787). I used the exact code reprogramming the default values for the password and censorship mode. The only difference was that I set the SLOCK/SSLOCK bits manually opposed to the 0x800FFFFF value they listed.
This unfortunately bricked my chip. It is stuck in censored mode and the password is corrupted. I cannot attach with the PEMicro even with the default, zero’d, and FF’d out values as the password.
How were you able to set the password and censorship mode on the chip? Was there some sort of application that you used, or did you write it into the application code? And if you did implement it in code could you provide it?
Also, in your BAM BAM whitepaper is it correct to assume that all of your successful attempts were done with a custom password and censorship mode enabled? Thanks