Hello,
I am trying to break the DES round 1 key based on my own captures, however, I am having issues doing so.
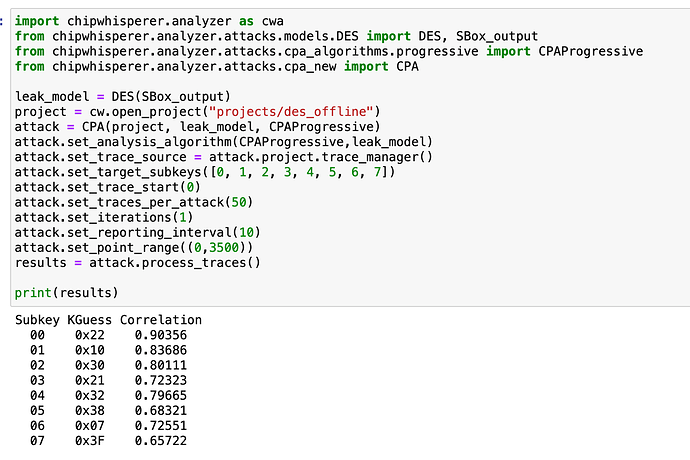
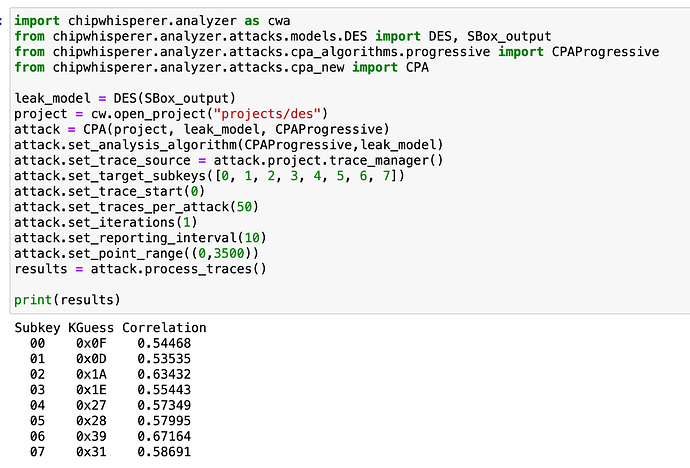
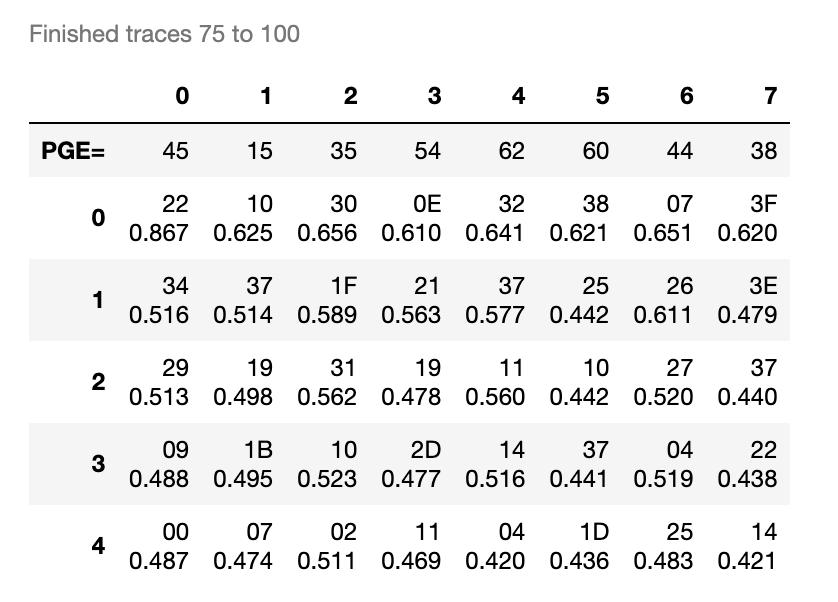
First, just to prove that my attack works, I am using traces supplied by CW software. The original key is 2B 7E 15 16 28 AE D2 A6
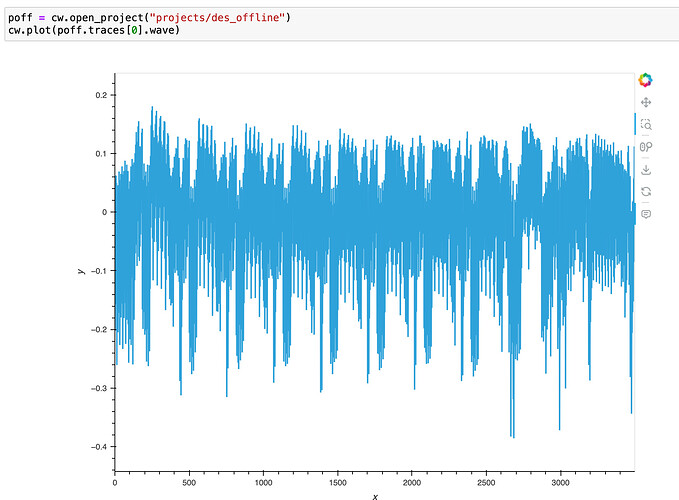
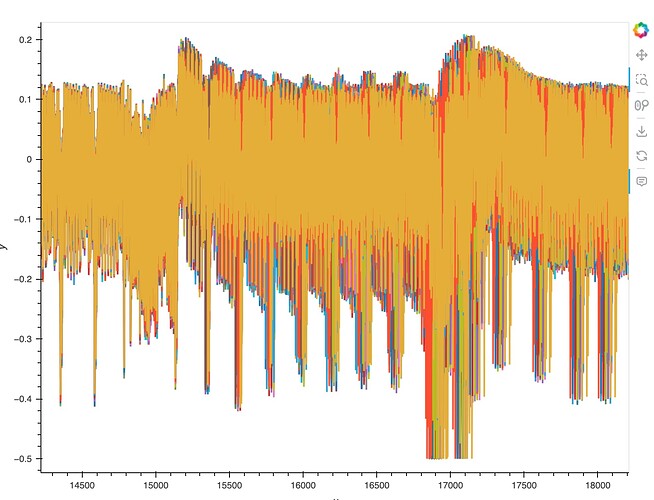
This all looks good. The offline traces look like this:
To capture my own, I am using the following capture function:
scope.adc.samples = 3500
scope.adc.offset = 14000
import random
def get_rand_bytes(n):
return random.randbytes(n)
def capture_traces(cmd, data):
target.flush()
scope.arm()
target.send_cmd(cmd, 0, data)
capture = scope.capture()
if capture:
print("Timeout")
data = target.read_cmd('r')
trace = scope.get_last_trace()
return data, trace
Then the capture itself:
#Set your project name here
project = cw.create_project("projects/des", overwrite = True)
#Set your number of traces here
num_traces = 50
target.flush()
target.send_cmd("x", 0, [])
key = target.read_cmd('r')
print_output(key)
for i in trange(num_traces):
pt = get_rand_bytes(8)
dout, trace = capture_traces('p',pt)
print(pt.hex(" ",1).upper())
if trace is None:
print("No trace captured")
continue
ptrace = cw.Trace(trace,pt,dout[3:-2],key)
project.traces.append(ptrace)
project.save()
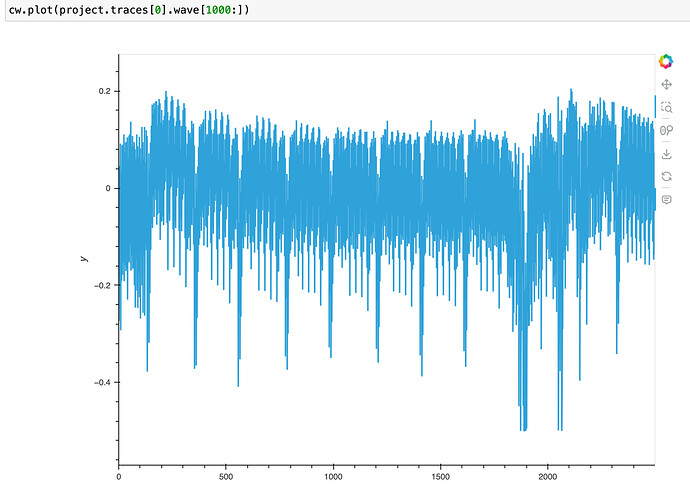
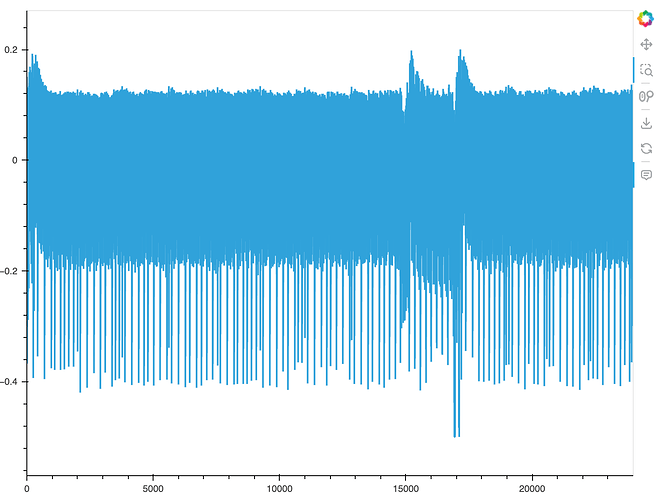
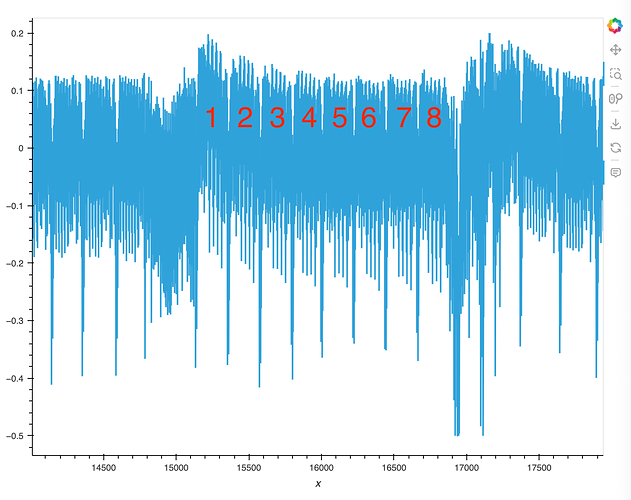
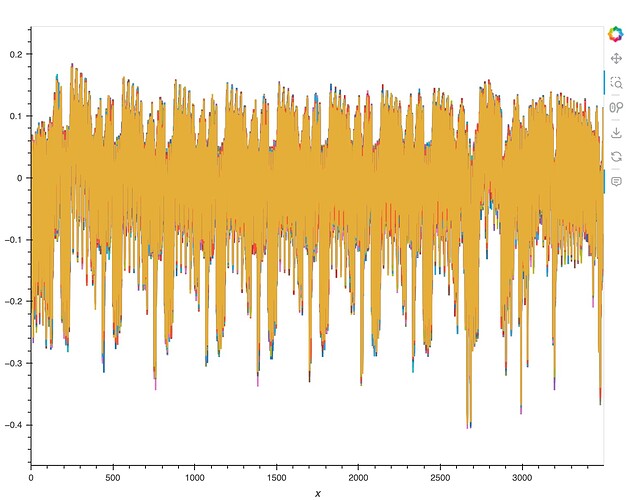
The trace looks like this:
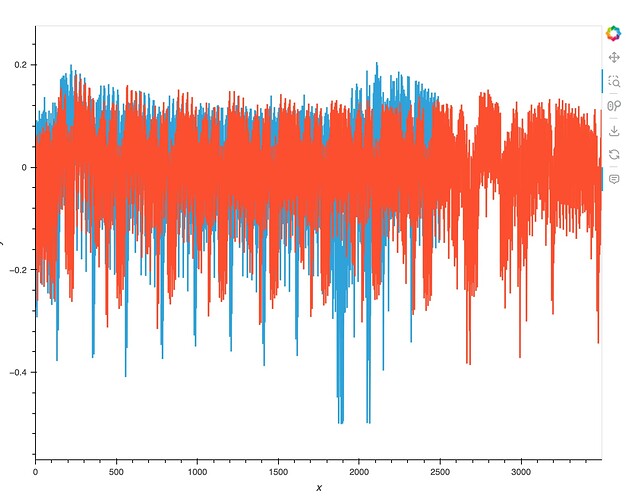
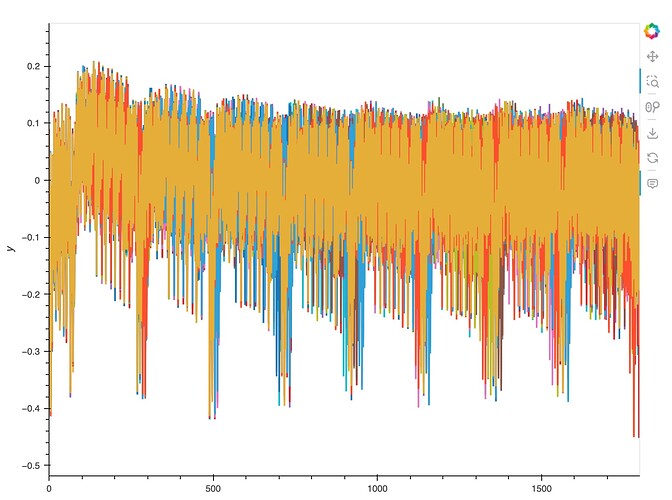
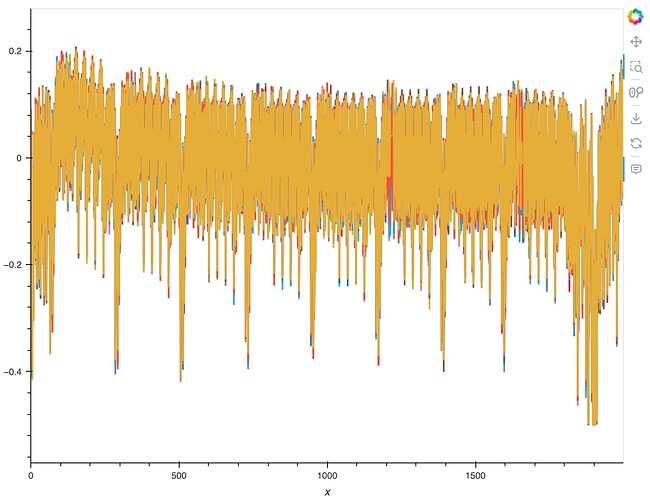
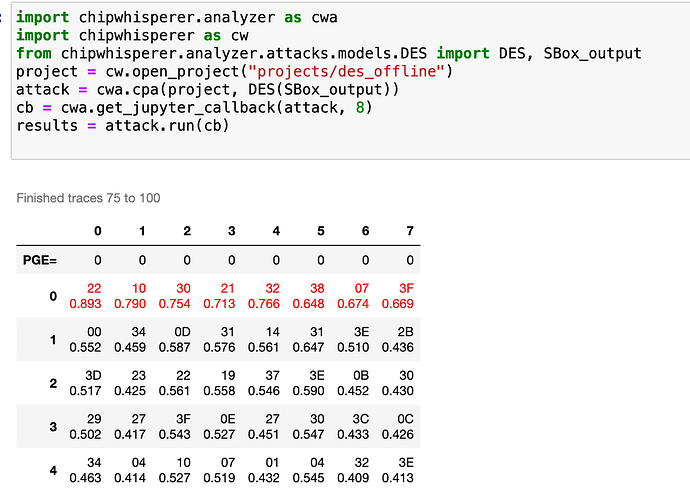
If I overlay offline over my own, I get this:
And the correlation doesn’t work. Not sure what’s happening.
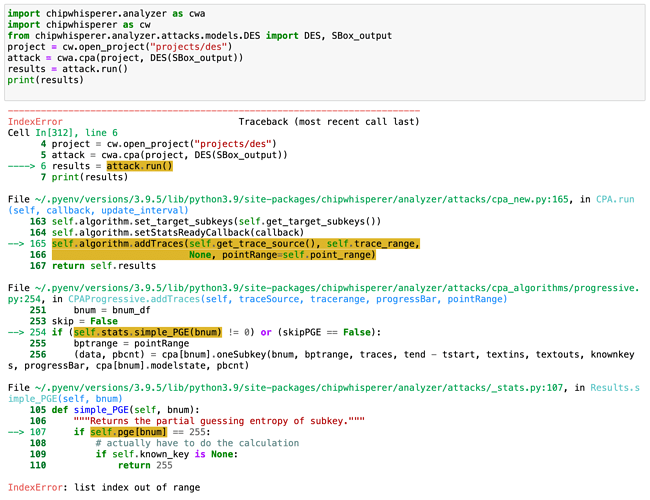
If I use a simpler method to crack the key, it completely errors out (but works with offline traces).
Any advice or what I could look at ?