Oops, my mistake! Sorry for the confusion.
The counter is typically much wider than 1 byte, since a one-byte counter would only allow 255 16-byte words to be encrypted before the counter repeats itself (which would be very bad). The counter width is typically defined by the protocol. But otherwise you have the right idea.
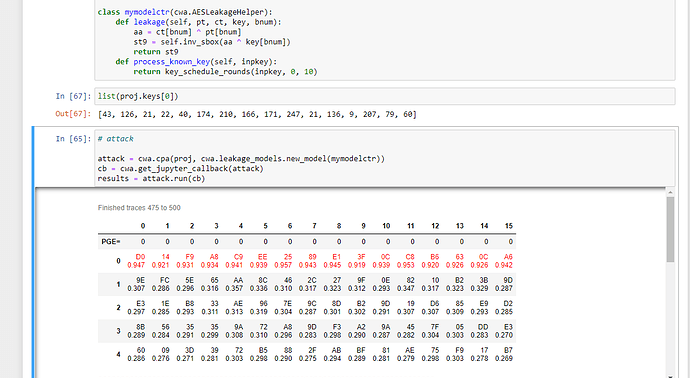
I hadn’t looked at your screenshot before – it looks like you’re doing everything exactly right there. The red-colored bytes are the correct key bytes. Your attack succeeded. The reason they are [D0, 14…] instead of [2B, 7E,…] is because you’re attacking the round 10 key (AES key schedule - Wikipedia).
See for yourself:
import chipwhisperer as cw
import chipwhisperer.analyzer as cwa
inputkey = [0x2b, 0x7e, 0x15, 0x16, 0x28, 0xae, 0xd2, 0xa6, 0xab, 0xf7, 0x15, 0x88, 0x09, 0xcf, 0x4f, 0x3c]
outputkey = [0xD0, 0x14, 0xF9, 0xA8, 0xC9, 0xEE, 0x25, 0x89, 0xE1, 0x3F, 0x0C, 0xC8, 0xB6, 0x63, 0x0C, 0xA6]
assert cwa.attacks.models.aes.key_schedule.key_schedule_rounds(inputkey, 0, 10) == outputkey