Hello,
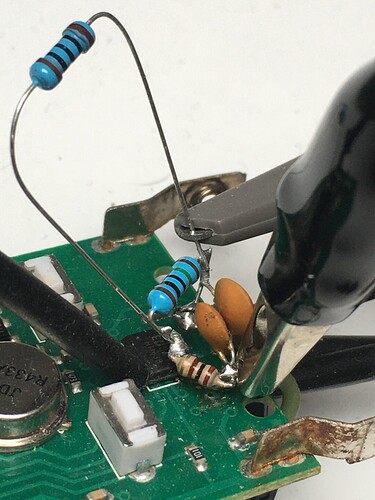
my overall plan is to analyze the remote control for my garage door, that is using the keeloq algorithm. So the attack will use the cipher output only.
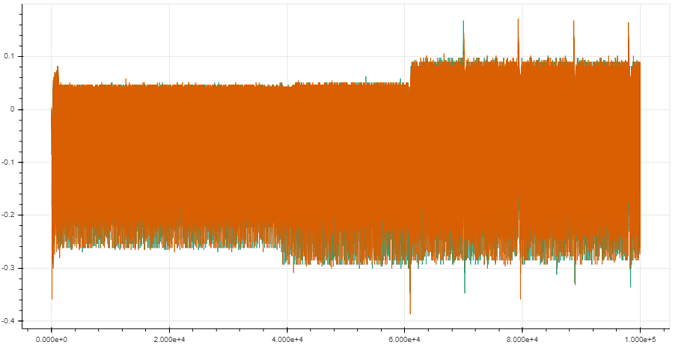
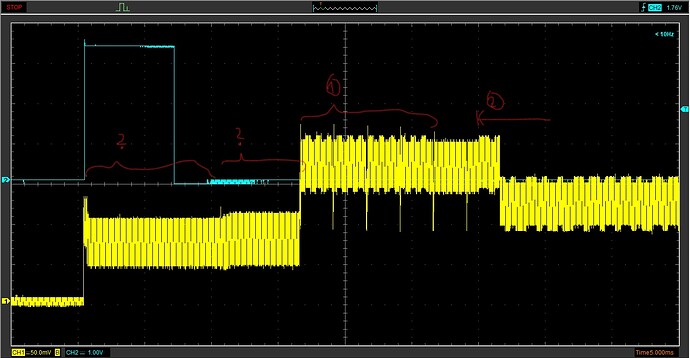
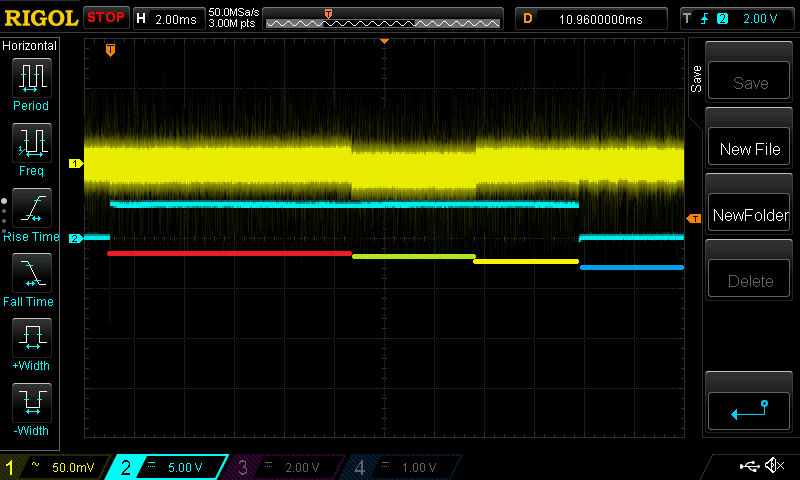
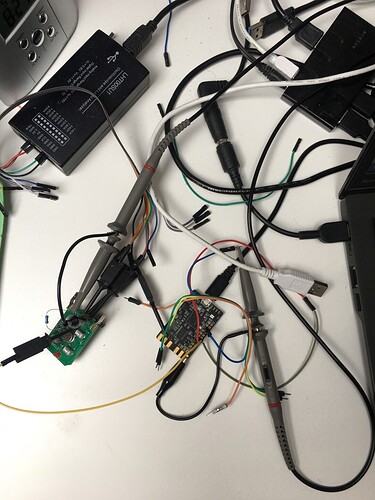
For this, I am using the cwnano at the maximum sampling rate (30Msps) and added some trigger offset in the ATSAM firmware to start sampling at specific points in time after “pressing” the remote control button using the cwnano’s GPIO4.
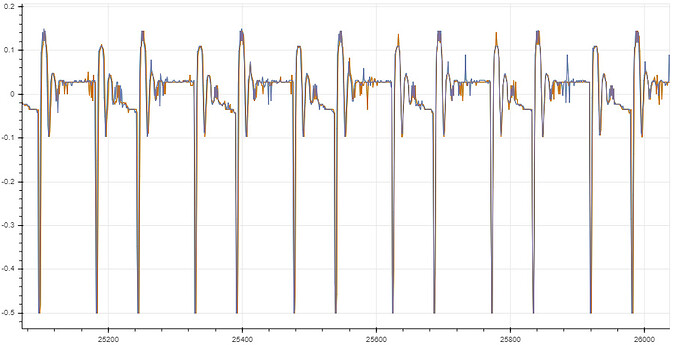
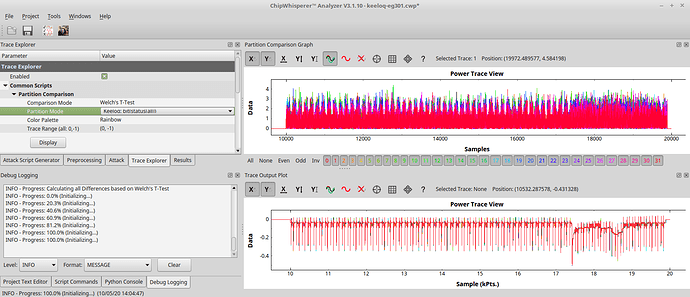
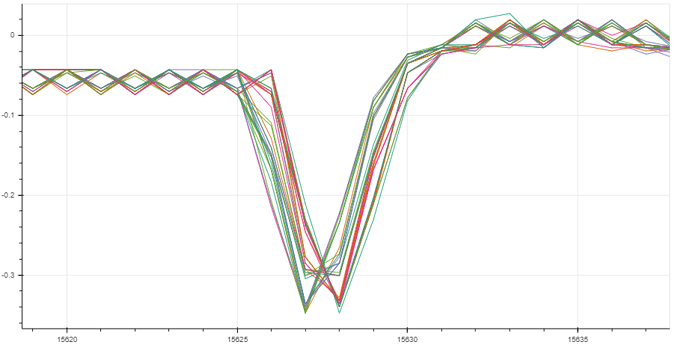
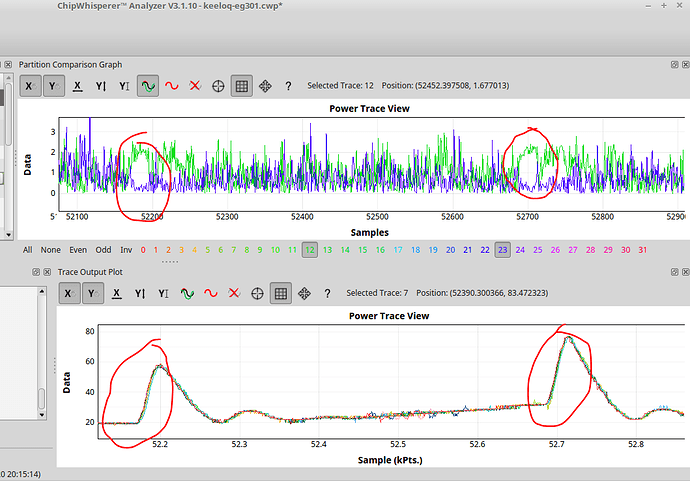
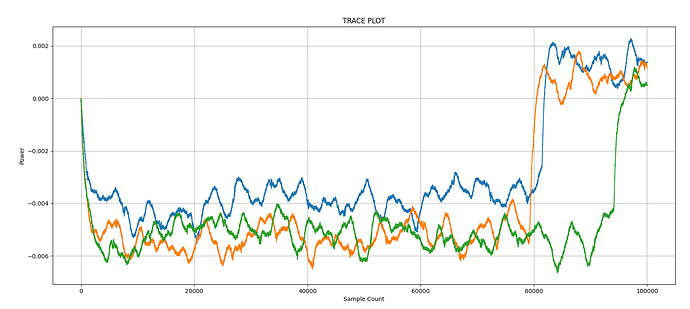
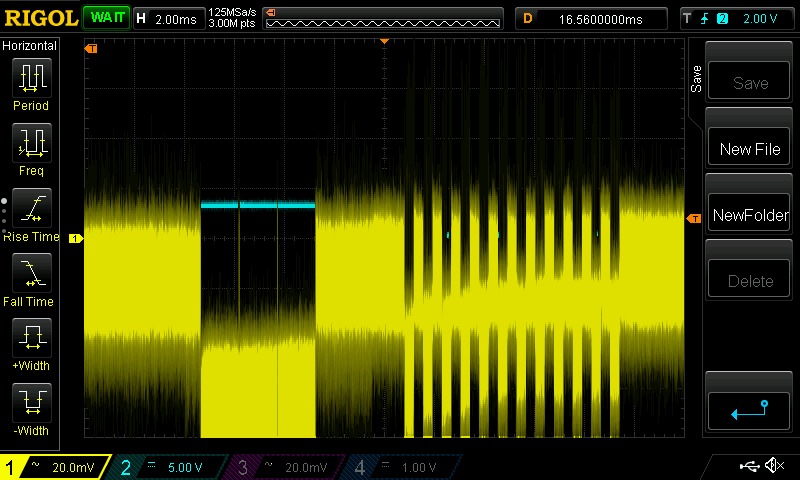
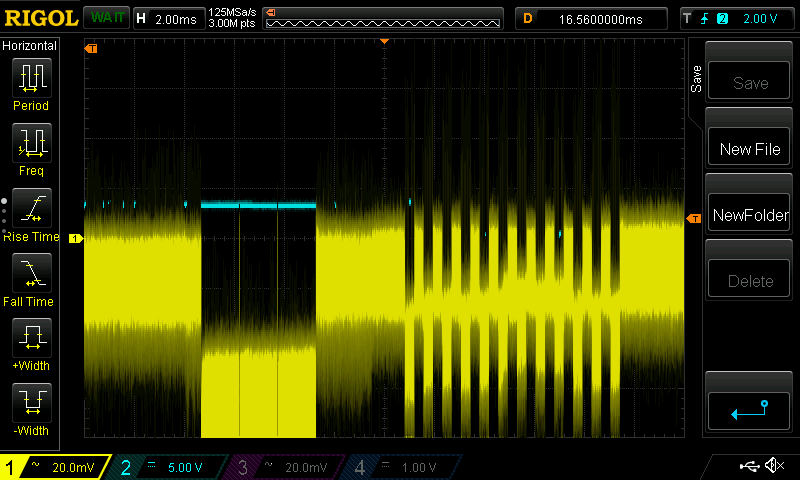
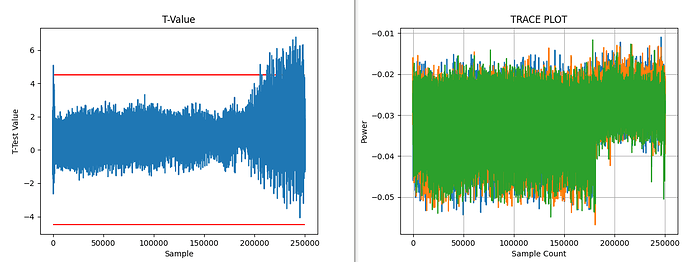
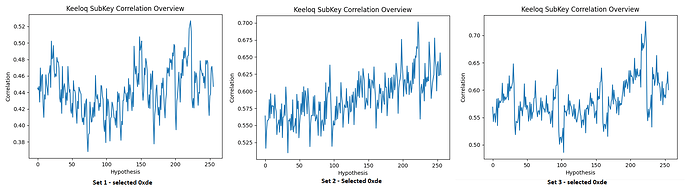
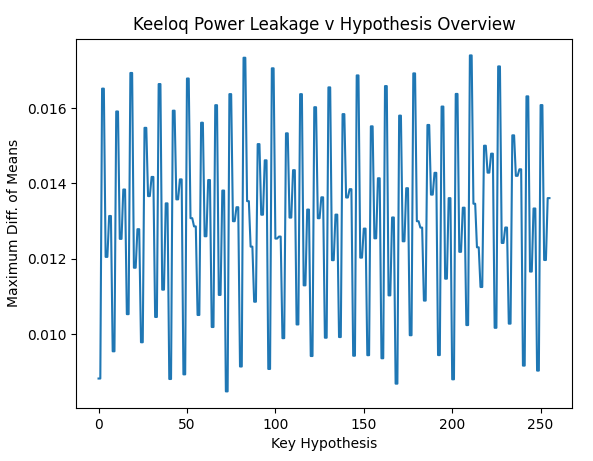
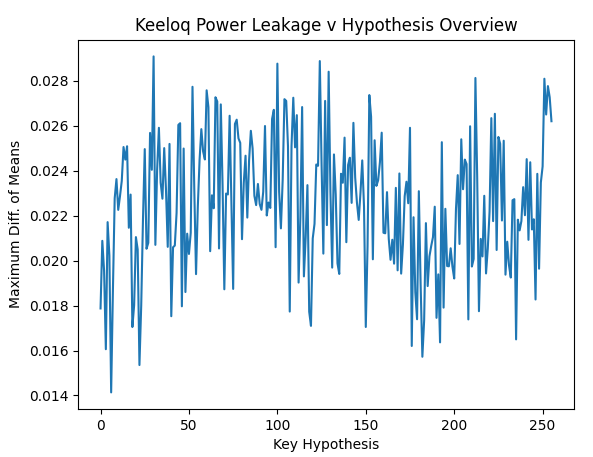
I have recorded 200 traces with 40k samples each. From pressing the button until the first rf pulse, >16 ms elapse, so I tried at two different offsets and want to see any correlation with the encrypted output. For other examples, I saw these rainbow color spikes, showing the sample positions where the 32 bits leak.
But so far my eyes see no rainbow colors ![]()
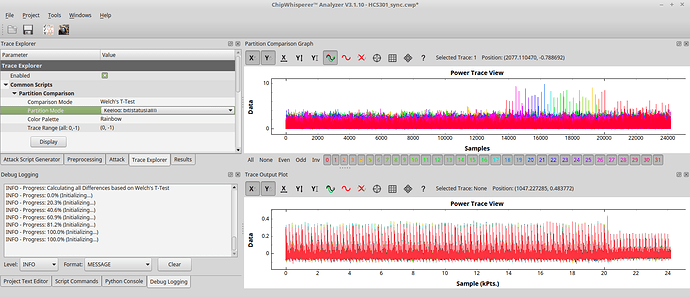
So I compare my situation to what this guy in 2016 did: chipwhisperer-marc/doc/marc/keeloq/examples_hcs301/examples_hcs301.md at master · marc-invalid/chipwhisperer-marc · GitHub
48Msps using the CW1002
The chip analysed there was the original microchip HCS301, runnint at ca. 1MHz
I am analyzing the EG301, a chinese clone: EG301 pdf, EG301 Description, EG301 Datasheet, EG301 view ::: ALLDATASHEET :::
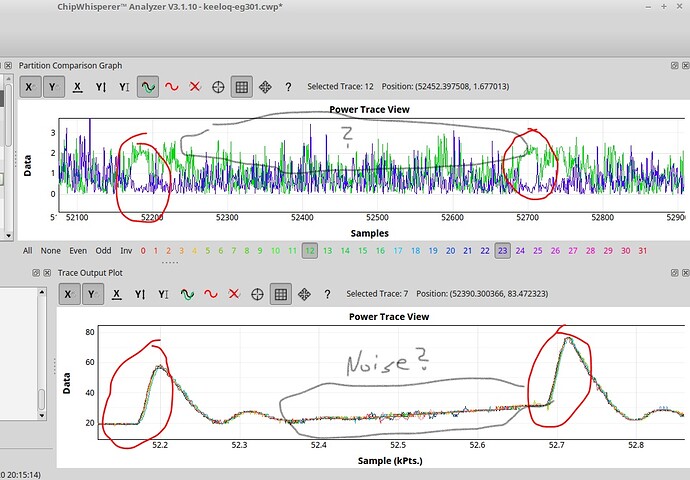
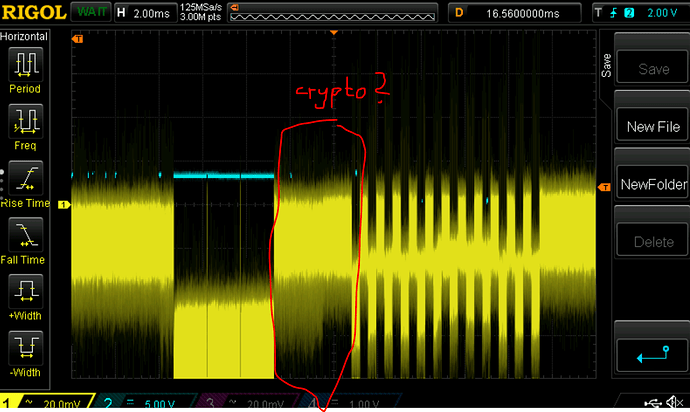
Also my power trace shows two clocks spikes fast, followed by little pause (2 clocks pe instruction?). Whereas the HCS301 shows four spikes going down (four clocks per instr.?).
Anyhow, the HCS seems to leak the bits at the second largest spike (out of the four).
This was kind of surprising to me today, since I was about to consider the maximums only.
What next?
- Does my powertrace look usable with respect to sampling frequency/resolution?
- Are some counteremeasures known, that might be implemented in this chip released in 2013?
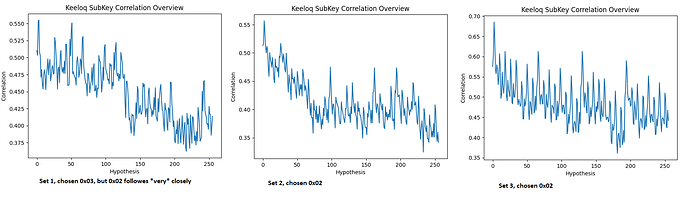
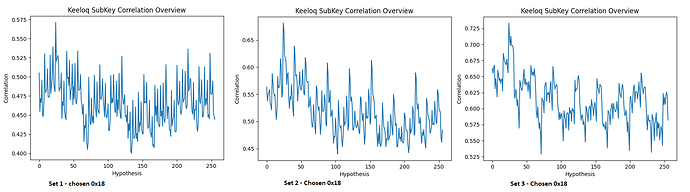
- Any hints, how to find the leaking samples when only the textout is known?
Regards,
Henning