For some reasons, support of DES SCA was completely dropped from the CW.
If I correctly remember, there were no attempts to add hardware DES. SCA attacks against hardware DES I found pretty interesting as:
- Leakage models are applicable very well to DES.
- Move from well known AES attacks to something new which can be implemented from very beginning.
So, I decided to use the PSOC62 SoC which has a rich set of HW crypto algorithms.
Writing the DES app was pretty straightforward, the little challenge was flashing the firmware using J-link. Infineon artificially enforces using its KitProg3 tool via the OpenOCD code.
To bypass it, I did a hack stored at jlink_psoc62_swd.cfg
source [find interface/jlink.cfg]
transport select swd
adapter speed 1000
# Override acquisition to work with J-Link
proc mxs40_acquire { target } {
echo "J-Link: Skipping acquisition (not needed/supported)"
return 1 # Return success to continue
}
# Source the original config
source [find target/infineon/cy8c6xx.cfg]
# Override the broken function
proc mxs40_reset_deassert_post { target_type target } {
echo "J-Link: Simplified reset for PSoC62"
# Skip KitProg3 acquisition check
if {[string match "psoc6*" $target_type]} {
# Just do basic reset, no acquisition
psoc6 reset_halt sysresetreq
}
}
init
reset init
echo "PSoC62 ready for programming with J-Link"
To burn the firmware via SWD and using J link, it is necessary to download Infineon OpenOCD go to its bin folder and then run openocd -f ../jlink_psoc62_swd.cfg.
Then run telnet localhost 4444 in another console and burn the firmware from there
flash write_image erase /Users/username/simpleserial-des/simpleserial-des-CW308_PSOC62.hex
reset run
the expected output is
auto erase enabled
Flash write discontinued at 0x10008270, next section at 0x1000a000
Padding image section 0 at 0x10008270 with 400 bytes (bank write end alignment)
[100%] [################################] [ Erasing ]
[100%] [################################] [ Programming ]
Padding image section 1 at 0x1000dba4 with 92 bytes (bank write end alignment)
[100%] [################################] [ Erasing ]
[100%] [################################] [ Programming ]
wrote 49152 bytes from file /Users/username/simpleserial-des/simpleserial-des-CW308_PSOC62.hex in 1.061066s (45.238 KiB/s)
I think it worth to highlight it, as this can be a real limitation of using the target board based on PSOC62.
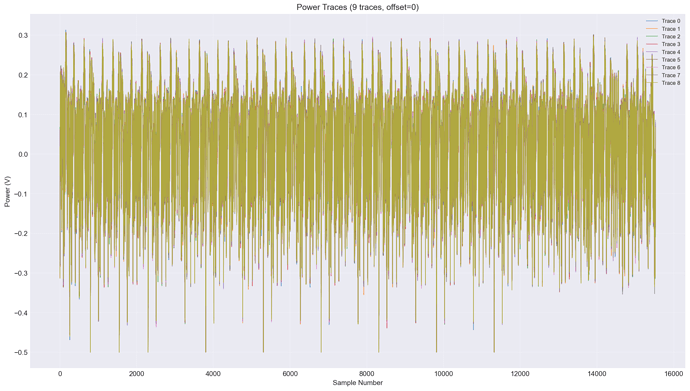
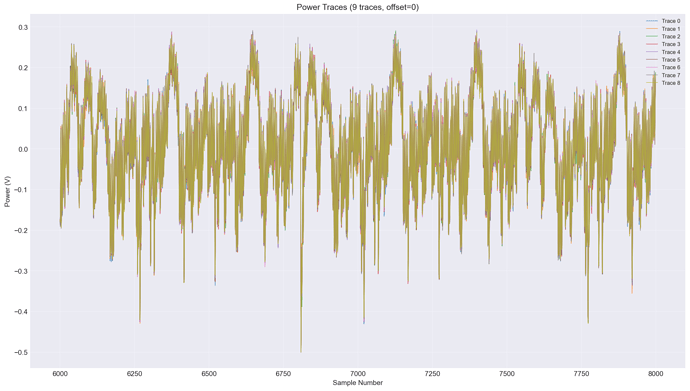
The DES power traces I captured:
- Complete traces:
- Zoomed in:
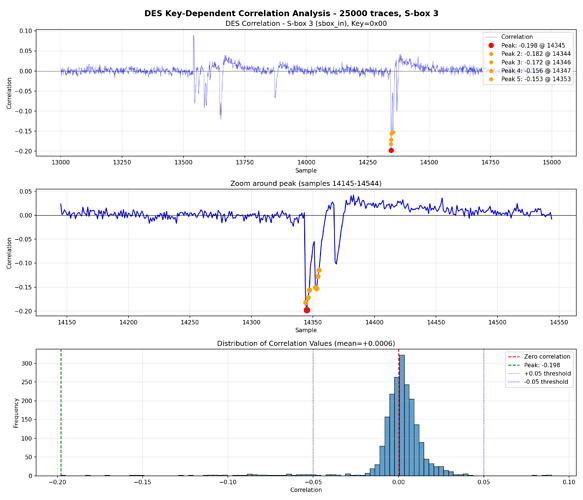
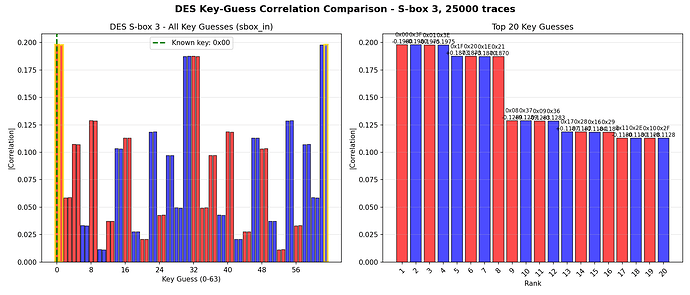
Next steps are write the leak models and scan the whole range for potential leakages to run the CPA attack there.