Hello,
We’re currently trying to extract the correct AES key using Differential Power Analysis (DPA) on firmware implementations. Unfortunately, despite numerous attempts, we’re unable to retrieve the full correct key.
We’ve tested both crypto targets (TinyAES128C and AVRCryptoLab) and collected datasets with 2,500 and 10,000 traces for each. Our primary suspicion is that we’re running into issues with ghost peaks.
We’ve followed the windowing suggestions from the lab solution, but we’re unsure which graph to use to determine the cycle offset and sample begin values. Specifically:
-
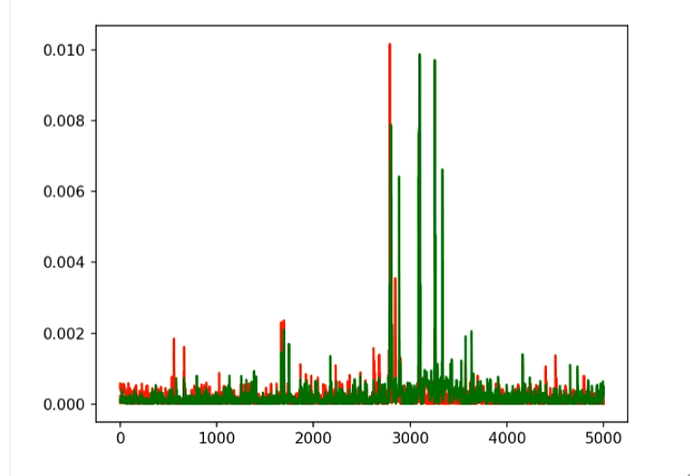
We tried using the graph generated by a single subkey hypothesis (showing ghost peaks and the correct key), like this:
-
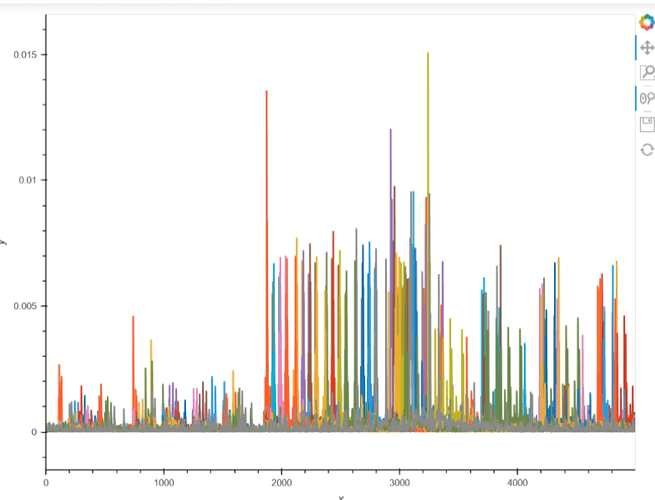
We also tried using the graph that includes all subkey guesses along with the correct key, like this:
We’ve experimented with a wide range of offsets and sample begin values, but the best result we’ve achieved so far is 13/16 correct key bytes.
So our questions are:
- Which graph should we be using to determine the cycle offset and sample begin?
- How do we decide which peak to consider? How “tall” does a peak need to be for it to be meaningful or worth zooming in on?
- Are there any additional tips to deal with ghost peaks more effectively?
We’d really appreciate any advice or clarification. Thanks in advance!