Wan to carify
But it IS when selected tio2, whay I noticed is that it only is up 100ns (maybe is a bit too low isn’t??):
Here I was trying to say that triggering with tio2 is working as expected, the trigger can be seen on the logic analyzer, but wanted to know if his duration (100ns) is the exected one by curiosity and also wanted to ask, why not, if we can change the trigger duration maybe make it a little bit longer like 1ms or so…
So lets start with the minimal reproducible:
I also made a video to show you what I’m doing and how I’m doing it, maybe it can also help to see wwhat is happening ;D
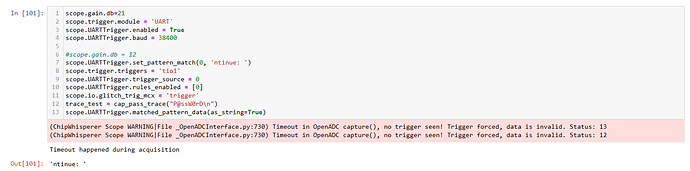
I’m trying to capture using UART triggering with the husky using the SAM4S as target in the notebook Lab 2_1B - Power Analysis for Password Bypass, I am able to capture using TIO2 as source trigger, but each time I try to use TIO1 as source the notebook fails with no trigger seen! Trigger forced
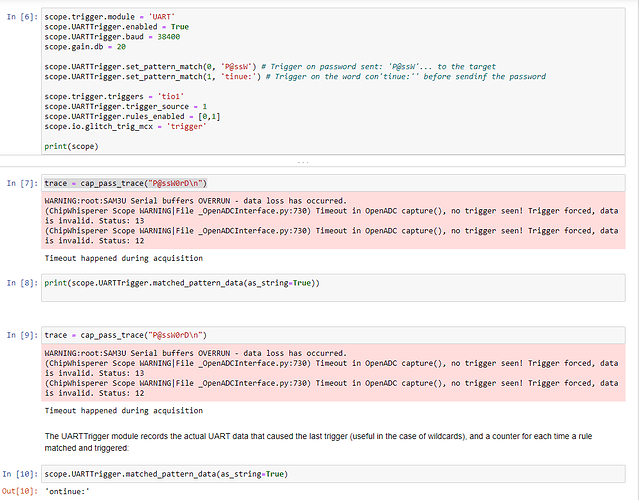
the Notebook is this:
SCOPETYPE="OPENADC"
PLATFORM='CW308_SAM4S'
CRYPTO_TARGET='NONE'
VERSION='HARDWARE'
%run "Lab 2_1B - Power Analysis for Password Bypass (HARDWARE).ipynb"
reset_target(scope)
scope.trigger.module = 'UART'
scope.UARTTrigger.enabled = True
scope.UARTTrigger.baud = 38400
scope.gain.db = 12
scope.UARTTrigger.set_pattern_match(0, 'P@ssW') # match 'P@ssW'... that we send
scope.UARTTrigger.set_pattern_match(1, 'ontinue:') # match 'ontinue'... that we receive
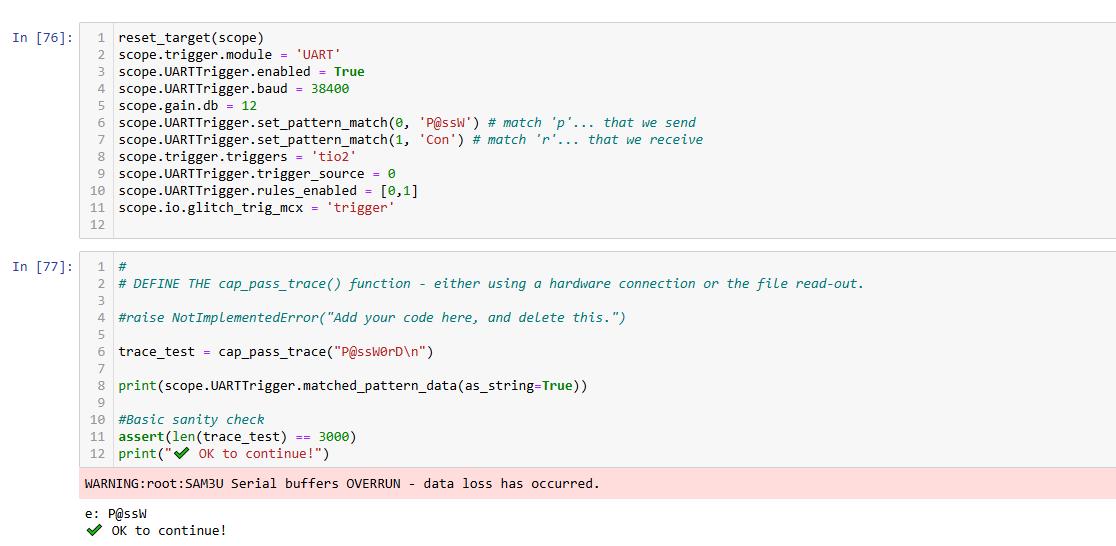
scope.trigger.triggers = 'tio2'
scope.UARTTrigger.trigger_source = 0
scope.UARTTrigger.rules_enabled = [0,1]
scope.io.glitch_trig_mcx = 'trigger'
(ChipWhisperer Scope WARNING|File TraceWhisperer.py:1367) Coudln’t achieve exact desired frequency (129981170.654297); setting to 130207492.828369 instead.
trace_test = cap_pass_trace("P@ssW0rD\n")
print(scope.UARTTrigger.matched_pattern_data(as_string=True))
WARNING:root:SAM3U Serial buffers OVERRUN - data loss has occurred.
ue:P@ssW
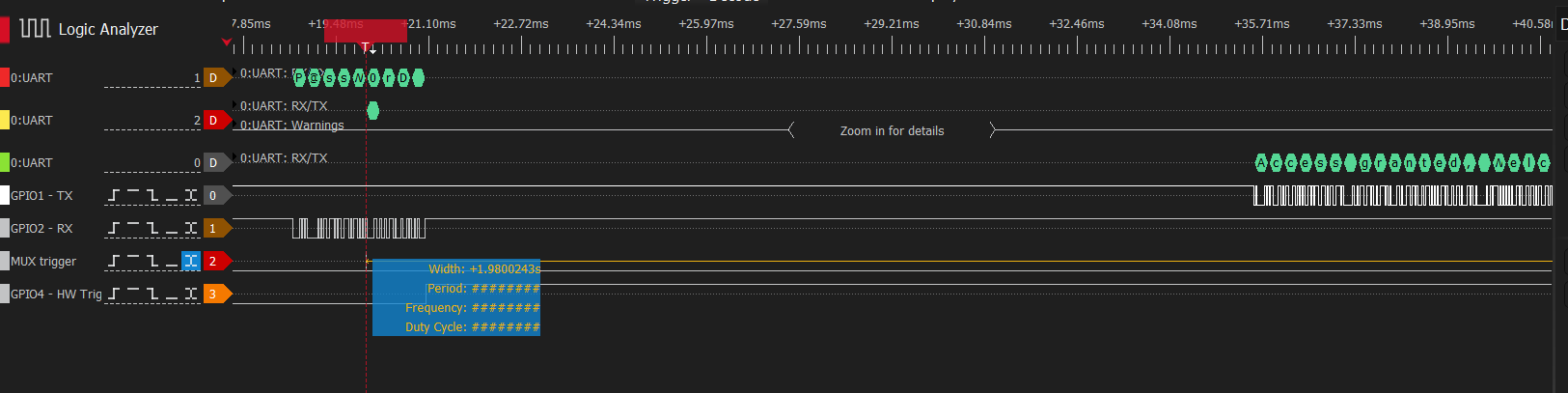
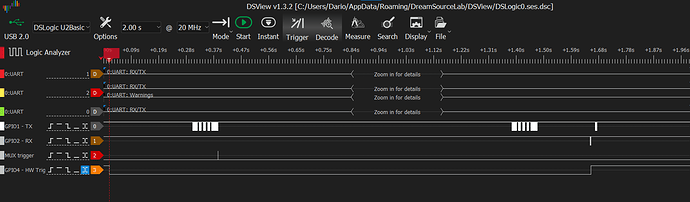
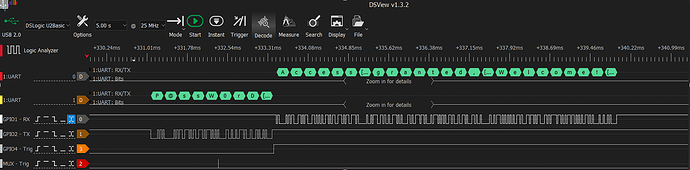
While running this code I have the logic analyzer connected to the MUX and to GPIO4, plus GPIO1 and GPIO2, and now it is configured to capture at any change of state at pin GPIO4
In this screenshot we can see the trigger on the MUX and also the trigger on GPIO4
few moments later so the capture with Tio2 is working propery:
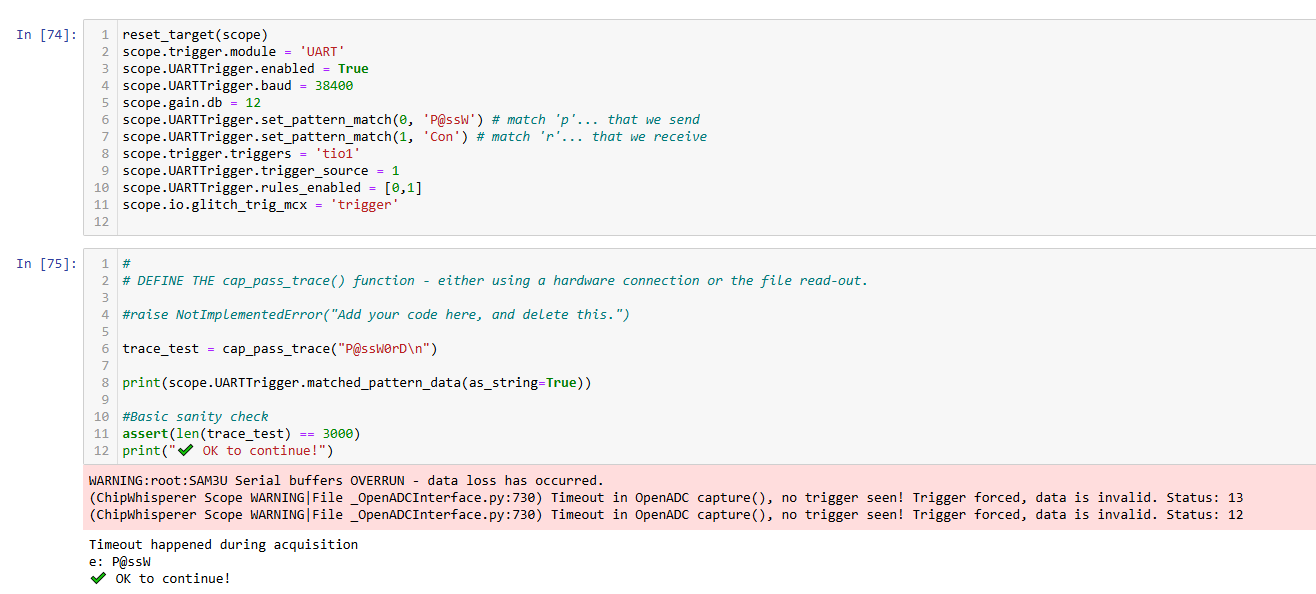
After this the next cell is the capture with Tio1:
reset_target(scope)
scope.trigger.module = 'UART'
scope.UARTTrigger.enabled = True
scope.UARTTrigger.baud = 38400
scope.gain.db = 12
scope.UARTTrigger.set_pattern_match(0, 'P@ssW') # match 'P@ssW'... that we send
scope.UARTTrigger.set_pattern_match(1, 'ontinue:') # match 'ontinue:'... that we receive
scope.trigger.triggers = 'tio1'
scope.UARTTrigger.trigger_source = 1
scope.UARTTrigger.rules_enabled = [0,1]
scope.io.glitch_trig_mcx = 'trigger'
trace_test = cap_pass_trace("P@ssW0rD\n")
print(scope.UARTTrigger.matched_pattern_data(as_string=True))
WARNING:root:SAM3U Serial buffers OVERRUN - data loss has occurred.
(ChipWhisperer Scope WARNING|File _OpenADCInterface.py:730) Timeout in OpenADC capture(), no trigger seen! Trigger forced, data is invalid. Status: 13
(ChipWhisperer Scope WARNING|File _OpenADCInterface.py:730) Timeout in OpenADC capture(), no trigger seen! Trigger forced, data is invalid. Status: 12
Timeout happened during acquisition
ontinue:*
Here we see that ontinue:* is printed as result of the command print(scope.UARTTrigger.matched_pattern_data(as_string=True)) which indicates configured pattern matching
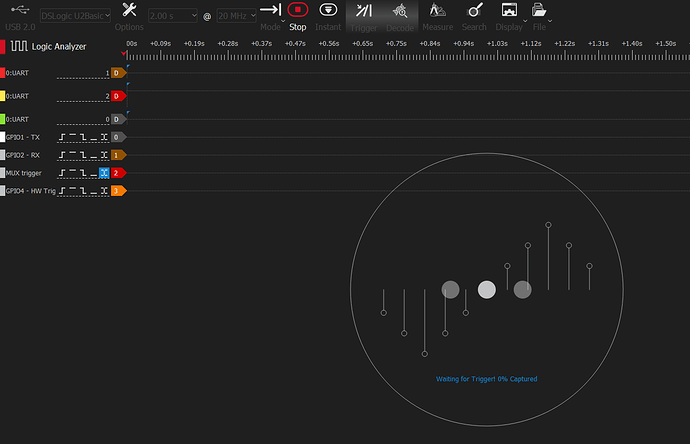
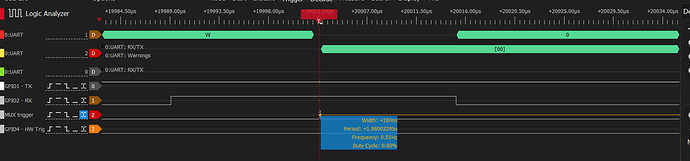
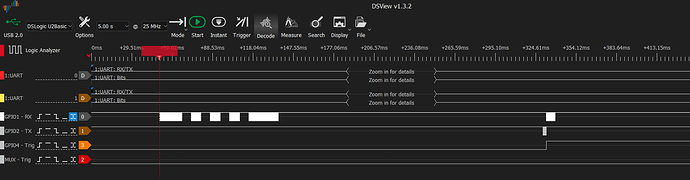
What is more extrange is that running this cell with the logic analyzer attached many times does not trigger the MUX trigger nor the GPIO4, as it were executing nothing at all…
This is the logic analyzer screen after runnin this cell and being configured to take a capture at state change of MUX pin:
The capture was not taken by the logic analyzer and the result of the notebok’s cell was:
WARNING:root:SAM3U Serial buffers OVERRUN - data loss has occurred.
(ChipWhisperer Scope WARNING|File _OpenADCInterface.py:730) Timeout in OpenADC capture(), no trigger seen! Trigger forced, data is invalid. Status: 13
(ChipWhisperer Scope WARNING|File _OpenADCInterface.py:730) Timeout in OpenADC capture(), no trigger seen! Trigger forced, data is invalid. Status: 12
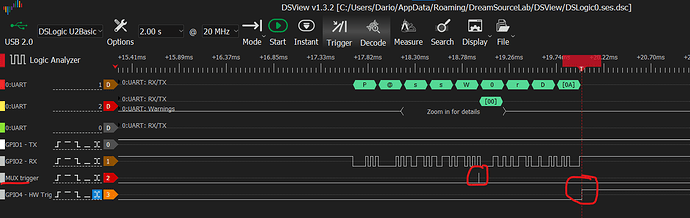
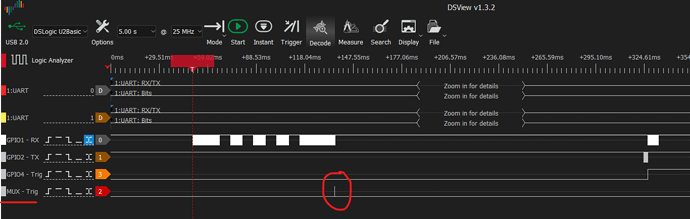
This is the screen of the logic analyzer configured to take a capture at change of state of the GPIO4 pin:
We now can see the trigger happening on MUX where it is supposed to happen which have no much sense to me as before the logic analyzer was configured to trigger on MUX and the logic analyzer got nothing, the cell result is still the same as before
no trigger seen! Trigger forced
- This is the %run “Lab 2_1B - Power Analysis for Password Bypass (HARDWARE).ipynb” code:
def cap_pass_trace(pass_guess):
reset_target(scope)
num_char = target.in_waiting()
while num_char > 0:
target.read(num_char, 10)
time.sleep(0.01)
num_char = target.in_waiting()
scope.arm()
target.write(pass_guess)
ret = scope.capture()
if ret:
print('Timeout happened during acquisition')
trace = scope.get_last_trace()
return trace
This is the firmware flashed to the SAM4S:
int main(void)
{
platform_init();
init_uart();
trigger_setup();
char passwd[32];
char correct_passwd[] = "P@ssW0rD";
//trigger_low();
delay_2_ms();
delay_2_ms();
//trigger_high();
while(1){
my_puts("*****Safe-o-matic 3000 Booting...\n");
//Print some fancy-sounding stuff so that attackers
//will get scared and leave us alone
my_puts("Aligning bits........[DONE]\n");
delay_2_ms();
my_puts("Checking Cesium RNG..[DONE]\n");
delay_2_ms();
my_puts("Masquerading flash...[DONE]\n");
delay_2_ms();
my_puts("Decrypting database..[DONE]\n");
delay_2_ms();
my_puts("\n\n");
//Give them one last warning
my_puts("WARNING: UNAUTHORIZED ACCESS WILL BE PUNISHED\n");
trigger_low();
//Get password
my_puts("Please enter password to continue: ");
my_read(passwd, 32);
int len_pwd =sizeof(correct_passwd);
uint8_t passbad = 0;
trigger_high();
for(uint8_t i = 0; i < len_pwd; i++){
if (correct_passwd[i] != passwd[i]){
passbad = 1;
break;
}
}
if (passbad){
//Stop them fancy timing attacks
int wait = 1;
for(volatile int i = 0; i < wait; i++){
;
}
delay_2_ms();
delay_2_ms();
my_puts("PASSWORD FAIL\n");
//led_error(1);
} else {
delay_2_ms();
delay_2_ms();
my_puts("Access granted, Welcome!\n");
//led_ok(1);
}
//All done;
while(1);
}
return 1;
}
If you need anything else please does not hesitate on asking for it