Hey,
I’m new to chipwhisperer and are a bit confused when it comes to the location of the “unknown key”. In the tutorials it seems like the unknown key is found and set with “key, text = ktp.next()” when creating new traces. Is this correct?
I am trying to implement AES256 with ecb and mbedtls. I have changed:
“simpleserial_addcmd(‘k’, 32, get_key);”
from 16 to 32 in simpelserial_aes.c
and
mbedtls_aes_setkey_enc(&ctx, key, 256);
from 128 to 256 in aes_independant.c.
are these changes correct?
So… where can i locate my secret key and change this key to 32 bits? I tried changing aes_independant.h to set a new key with no luck.
Best regards,
Fridthoy
1 Like
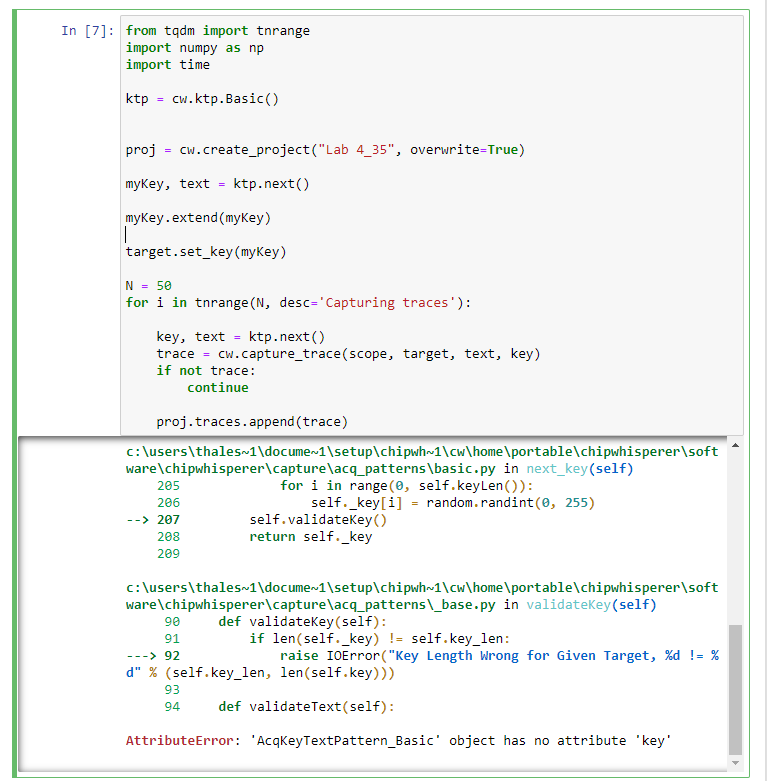
The key you get back from the ktp is just a bytearray, so probably the easiest way to extend it is key.extend(key).
You’ll probably want to remove the default key setting in simpleserial_aes.c, as the default key is 16 bytes long, which will probably mess things up as well.
Alex
Thank you!
I changed the defult key in aes-independant.h to a 32 bit key. I’m not sure if this alone will be able to run AES256.
I also tried to extend the key with key.extend(key). but got an error message.
I have a hard time wrapping my head around what exactly ktp is doing. It is creating a bytearray for the key and text. Why do I need this and why is it generating a lot of keys when I am only interested in one key (the unknown key) I am looking for?
Maybe a dumb question but I would apriciate an explination on capturing traces and ktp.Basic()
Best Regards
fridthoy
1 Like
The ktp by default is setup to generate a constant key, so it generates the same one every time. Try using ktp.next_text() in the loop instead of ktp.next().
Alex
Thanks for answering!
It seems like my results after attacking is only dependent on the key set in aes-independant.h… at least my answer when attacking is this key. The key I send in with ktp.next() seems to have no impact, how can this be?
1 Like
target.set_key() does check if the key you’re sending is the same as the last one, mostly to increase capture speed in the loop. Can you try using target.simpleserial_write('k', key) directly?
Alex
hmm, I tried using target.simpleserial_write('k', key) but it seems that the key is only dependent on the key written in aes-independant.h.
At least if I change the key in aes-independant.h the attack returns correct key. Changing the key with target.simpleserial_write('k', key) or sending a new key to the cw.capture_trace(scope, target, text, key) dosent seem to do anything, how can this be?
1 Like