Hello,
I am challenging the chipwhisperer tutorial of fault injection
Part 1, Topic 2: Clock Glitching to Bypass Password
I have completed the clock glitch in Topic1 and got the following results.
(The coordinates are below.)
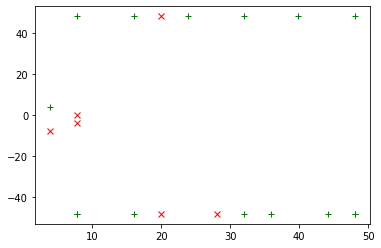
[[7.8125, -48.046875],
[7.8125, 48.046875],
[16.015625, -48.046875],
[23.828125, 48.046875],
[32.03125, -48.046875],
[32.03125, 48.046875],
[48.046875, -48.046875],
[48.046875, 48.046875],
[3.90625, 3.90625],
[7.8125, -48.046875],
[16.015625, 48.046875],
[35.9375, -48.046875],
[39.84375, 48.046875],
[44.140625, -48.046875],
[48.046875, -48.046875]]
Next I tried Topic2, but the glitch did not succeed.
I think the range of the glitch is correct, but what is the problem?
Sorry for the rudimentary question, but please let me know the hints.
I am using chipwhisperer XMEGA,
windows 10
and the follow is the glitch code used in Topic2
Thank you
from importlib import reload
import chipwhisperer.common.results.glitch as glitch
from tqdm.notebook import tqdm
import re
import struct
gc.set_range("width", 46, 49.8)
gc.set_range("offset", -46, -49.8)
gc.set_range("ext_offset", 11, 31)
step = 1
gc.set_global_step(step)
scope.glitch.repeat = 1
reboot_flush()
broken = False
for glitch_settings in gc.glitch_values():
scope.glitch.width = glitch_settings[0]
scope.glitch.offset = glitch_settings[1]
scope.glitch.ext_offset = glitch_settings[2]
if scope.adc.state:
print("Trigger still high!")
gc.add("reset", (scope.glitch.width, scope.glitch.offset, scope.glitch.ext_offset))
reboot_flush()
scope.arm()
target.simpleserial_write('p', bytearray([0]*5))
ret = scope.capture()
# True : timeout
# False : no timeout
val = target.simpleserial_read_witherrors('r', 1, glitch_timeout=10)
if ret == False:
if val['valid'] is False:
gc.add("reset", (scope.glitch.width, scope.glitch.offset, scope.glitch.ext_offset))
else:
if val['rv'] == 1: #for loop check
broken = True
gc.add("success", (scope.glitch.width, scope.glitch.offset, scope.glitch.ext_offset))
print(val['payload'])
print(scope.glitch.width, scope.glitch.offset, scope.glitch.ext_offset)
print("🔑", end="")
else:
gc.add("normal", (scope.glitch.width, scope.glitch.offset, scope.glitch.ext_offset))
print("Done glitching")