hello Dear forum
I came to you with a question.
i want build Another algortihm(Post Quantum Cryptography - SABER) in chipwhisperer for SCA Study
but i faced a problem
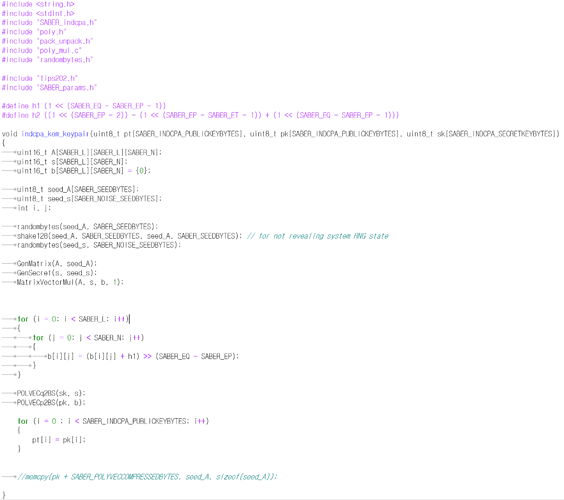
saber algorithm’s indcpa_public key byte is 992 bytes
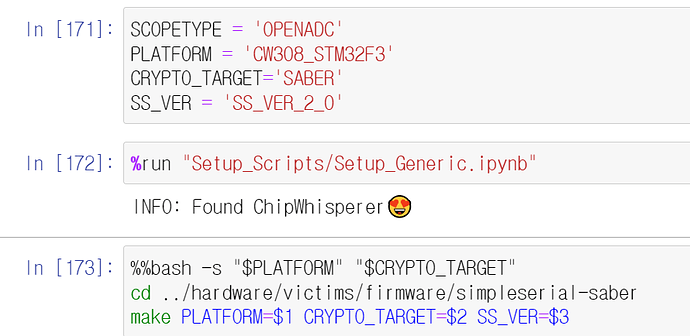
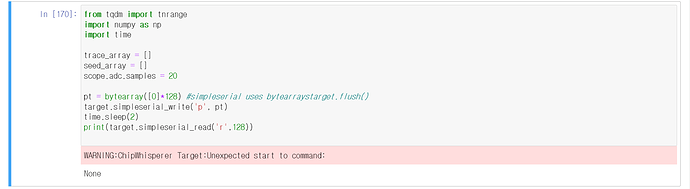
first question, i operated SS_VER_1, of course ver_1 can’t read that size
Similarly, I know that SS_VER_2 can only transmit up to 249Bytes per packet.
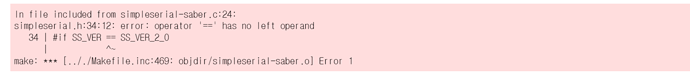
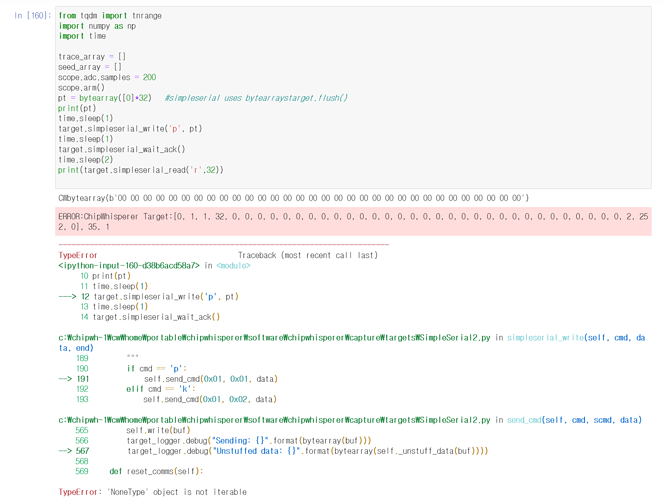
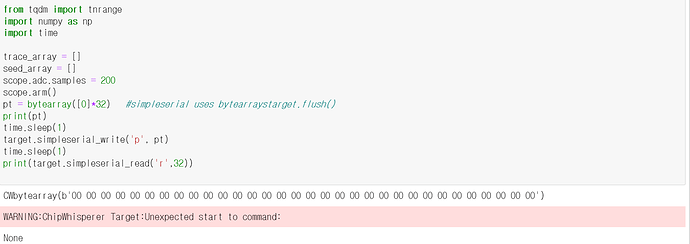
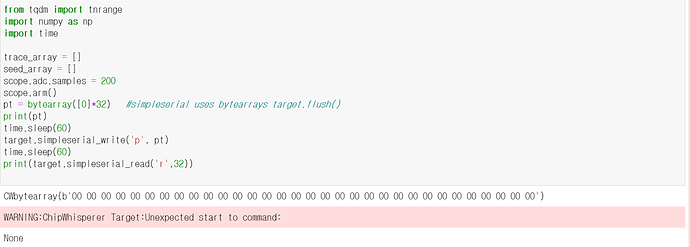
so i typed
and return this error
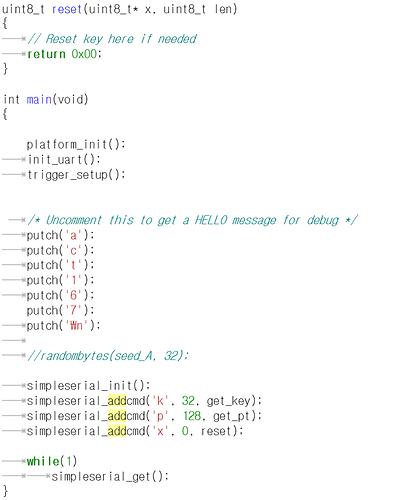
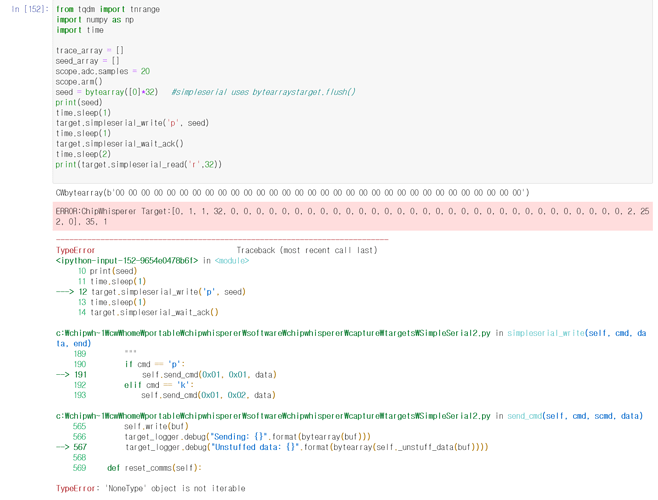
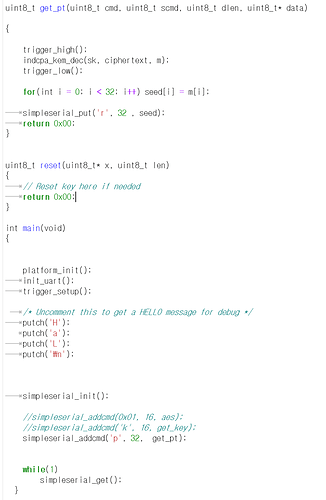
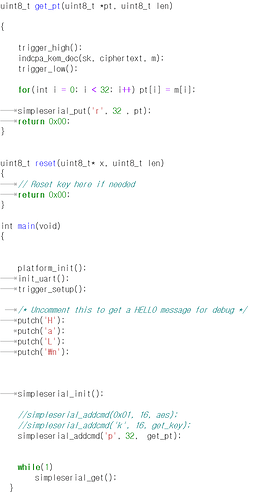
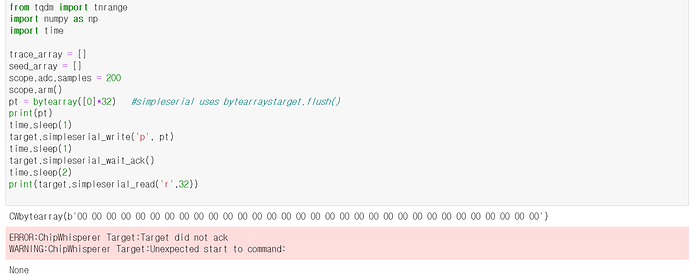
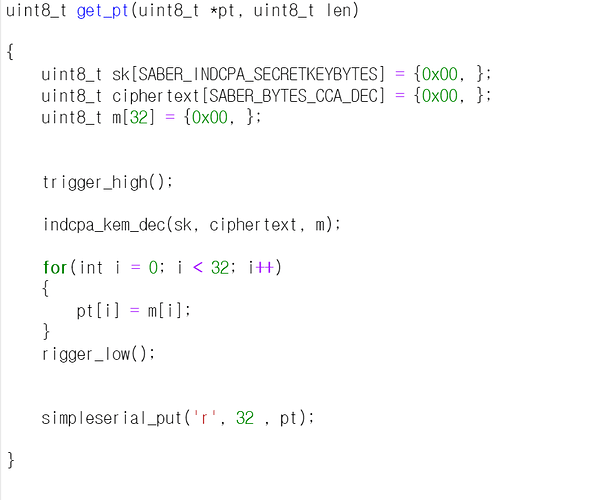
second question it is SS-saber(alias) code
and it is indcpa_kem_keypair() function
and i had this error
My guess is that this error is returned because the packet is oversized (992bytes). that’s right?
I thought 128 bytes would be returned, but it wasn’t.
And is it possible to split the packet and receive the ack?
thanks
gskim