After carefully following the instructions on how to capture a single trace which depicts the following operations :
-
16 XORs
-
16 register loads (this is the new IV being copied over)
-
Some serial communication
-
The signature check
-
The serial line going idle
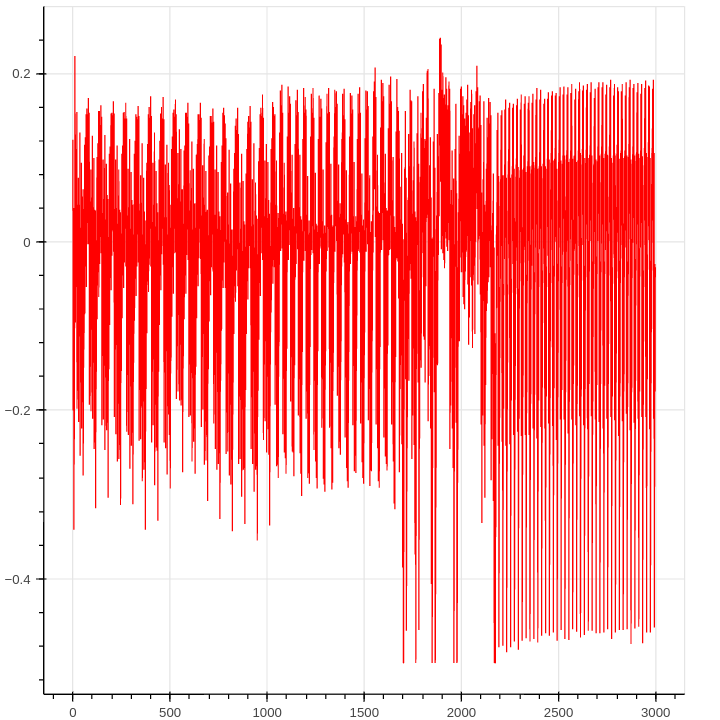
The trace looks fine as most of the operations are easily interpretable :
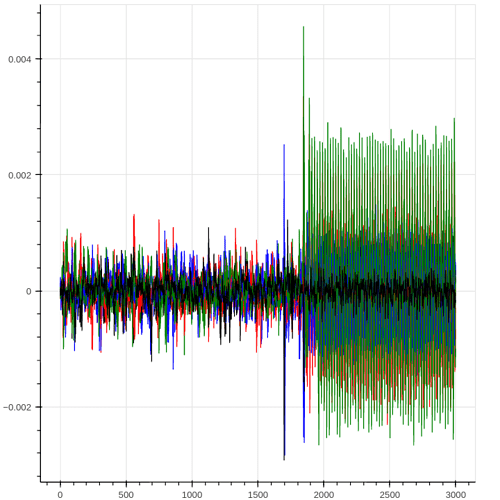
Then I capture 5000 traces(as I am attacking the XMEGA), the I try to locate the first XOR operation for the first byte of the IV(Initialization Vector) and then plot the difference of the two groups ( originating from the evaluation of the expression : DR[0] & (1 << bit) ) for each bit. I get something like this:
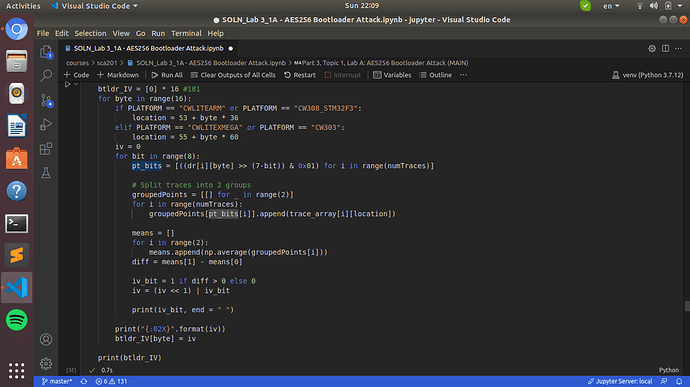
The when trying to run the function find_potential_xors, no matter how big I make the denominator of the threshold, some bytes of the IV have zero candidates for being the “plausible XOR points”.
Furthermore the method which repeats the conceptual 1-bit attack attack also fails when running the following block:
Sampling the correct XOR location fails resulting in recovering the completely wrong IV, although I’ve tried many different combinations, I could imagine to be reasonable for the location variable.
(p.s The key and signature attack of the AES-CBC worked great for me after some tweaking)