Things are looking much better! Thank you!
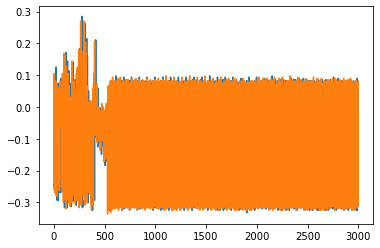
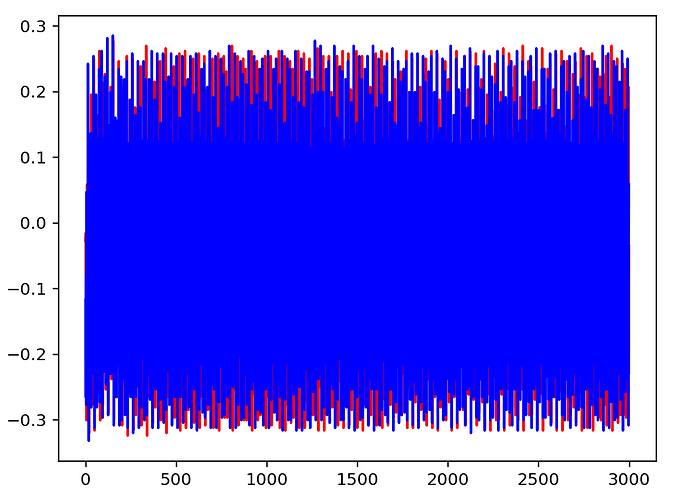
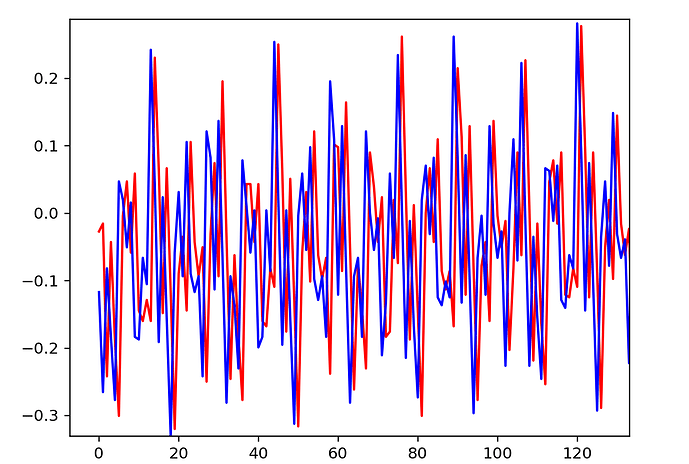
I ran the following two traces to see how well they overlap and it’s looking good!
import time
trace_h = cap_pass_trace("h\n")
trace_h2 = cap_pass_trace("h\n")
#print(trace_h)
%matplotlib notebook
import matplotlib.pylab as plt
plt.figure()
plt.plot(trace_h, 'r')
plt.plot(trace_h2, 'b')
plt.show()
I figured out a workaround for the errors I am seeing, and I think it’s because I have to do something extra to reset the target each time I send it the password.
The following error is what I kept running into before and what keeps coming up if I try to communicate with the target a second time. For instance, if I send the above block of code a second time.
Traceback (most recent call last):
File "/home/vagrant/work/projects/chipwhisperer/software/chipwhisperer/hardware/naeusb/naeusb.py", line 296, in txrx
response = self.usbdev().ctrl_transfer(payload[0], payload[1], payload[2], payload[3], payload[4], timeout=self._timeout)
File "/home/vagrant/.pyenv/versions/3.6.7/envs/cw/lib/python3.6/site-packages/pyusb-1.1.0-py3.6.egg/usb/core.py", line 1077, in ctrl_transfer
self.__get_timeout(timeout))
File "/home/vagrant/.pyenv/versions/3.6.7/envs/cw/lib/python3.6/site-packages/pyusb-1.1.0-py3.6.egg/usb/backend/libusb0.py", line 609, in ctrl_transfer
timeout
File "/home/vagrant/.pyenv/versions/3.6.7/envs/cw/lib/python3.6/site-packages/pyusb-1.1.0-py3.6.egg/usb/backend/libusb0.py", line 447, in _check
raise USBError(errmsg, ret)
usb.core.USBError: [Errno None] b'error sending control message: Broken pipe'
---------------------------------------------------------------------------
USBError Traceback (most recent call last)
~/work/projects/chipwhisperer/software/chipwhisperer/capture/targets/SimpleSerial.py in read(self, num_char, timeout)
239 num_char = self.ser.inWaiting()
--> 240 return self.ser.read(num_char, timeout)
241 except USBError:
~/work/projects/chipwhisperer/software/chipwhisperer/capture/targets/simpleserial_readers/_base.py in read(self, num, timeout)
133 # If we didn't get enough data, try to read more from the hardware
--> 134 data = bytearray(self.hardware_read(num, timeout=timeout)).decode('latin-1')
135 for c in data:
~/work/projects/chipwhisperer/software/chipwhisperer/capture/targets/simpleserial_readers/cwlite.py in hardware_read(self, num, timeout)
80 def hardware_read(self, num, timeout=250):
---> 81 return self.cwlite_usart.read(num, timeout)
~/work/projects/chipwhisperer/software/chipwhisperer/hardware/naeusb/serial.py in read(self, dlen, timeout)
185 if waiting > 0:
--> 186 newdata = self._usb.readCtrl(self.CMD_USART0_DATA, 0, min(waiting, dlen))
187 resp.extend(newdata)
~/work/projects/chipwhisperer/software/chipwhisperer/hardware/naeusb/naeusb.py in readCtrl(self, cmd, value, dlen)
701 # Vendor-specific, IN, interface control transfer
--> 702 return self.usbseralizer.readCtrl(cmd, value, dlen)
703
~/work/projects/chipwhisperer/software/chipwhisperer/hardware/naeusb/naeusb.py in readCtrl(self, cmd, value, dlen)
187 cmdpacket = self.make_cmd(self.READ_CTRL, cmdpacket)
--> 188 return self.process_rx(self.txrx(tx=cmdpacket))
189
~/work/projects/chipwhisperer/software/chipwhisperer/hardware/naeusb/naeusb.py in process_rx(self, inp)
153 if resp == self.ERROR:
--> 154 raise payload
155
USBError: [Errno None] None
During handling of the above exception, another exception occurred:
Warning Traceback (most recent call last)
<ipython-input-128-a9fa5eb8e085> in <module>
2
3 import time
----> 4 trace_h = cap_pass_trace("h\n")
5 trace_h2 = cap_pass_trace("h\n")
6 #print(trace_h)
<ipython-input-119-addfe96922f3> in cap_pass_trace(pass_guess)
3 num_char = target.in_waiting()
4 while num_char > 0:
----> 5 target.read(num_char, 10)
6 time.sleep(0.01)
7 num_char = target.in_waiting()
~/work/projects/chipwhisperer/software/chipwhisperer/capture/targets/SimpleSerial.py in read(self, num_char, timeout)
241 except USBError:
242 self.dis()
--> 243 raise Warning("Error in target. It may have been disconnected")
244 except Exception as e:
245 self.dis()
Warning: Error in target. It may have been disconnected
Just by chance I realized if I rerun the setup script it will communicate again.
%run "../../Setup_Scripts/Setup_Generic.ipynb"
It was so very confusing because I would run the check block:
#
# DEFINE THE cap_pass_trace() function - either using a hardware connection or the file read-out.
#
trace_test = cap_pass_trace("h\n")
#Basic sanity check
assert(len(trace_test) == 3000)
print("✔️ OK to continue!")
And it would complete perfectly with no errors. Then I would go to run my capture code:
import time
trace_h = cap_pass_trace("h\n")
trace_h2 = cap_pass_trace("h\n")
#print(trace_h)
%matplotlib notebook
import matplotlib.pylab as plt
plt.figure()
plt.plot(trace_h, 'r')
plt.plot(trace_h2, 'b')
plt.show()
And get that error every time. I will continue investigating why it seems to stop responding. The cap_pass_trace calls reset_target(scope) in it but obviously the Setup_generic.ipynb script is doing more. I will keep debugging and figure out what the difference is and why it’s locking.
Thank you very much for the help! I am excited to continue learning and move forward with the courses!
![]()

 OK to continue!”)
OK to continue!”)