Currently I am trying to attack a Hardware Implemented AES on an ATxmega32A4U.
In the archived wikia I found “Tutorial A6 Replication of Ilya Kizhvatov’s XMEGA® Attack” which pretty much explains how such an attack is performed.
However, the ChipWhisperer API got updated in the last versions and I am not quite sure where to implement the attack script in order to run the attack succesfully. I found the SBoxInputSuccessive to be a pretty similar leakage model, so I changed it up to:
class SBoxInputSuccessive(AESLeakageHelper):
name = ‘HD: AES SBox Input i to i+1’
c_model_enum_value = 4
c_model_enum_name = ‘LEAK_HD_SBOX_IN_SUCCESSIVE’
def leakage(self, pt, ct, key, bnum):
if bnum < 1 or bnum > 15:
raise ValueError("bnum should be in the range of 1 to 15")
if bnum == 1:
st1 = pt[bnum - 1] ^ 0x3b
st2 = pt[bnum] ^ key[bnum]
else:
st1 = pt[bnum - 1] ^ key[bnum - 1]
st2 = pt[bnum] ^ key[bnum]
return st1 ^ st2
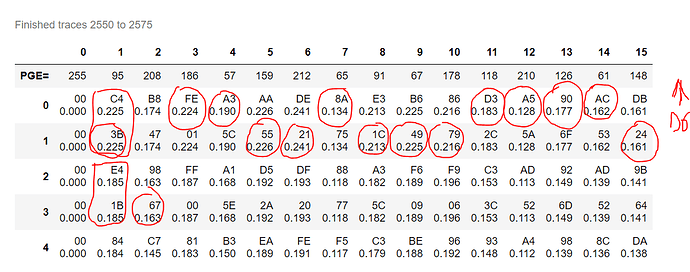
But the results as shown in the picture are not as expected. I also don’t know where the actual guess is happening since leakage is not supposed to take “guess” as parameter. The red circles are the actual key and another problem is, that the correlations are always in pairs of two. The 00’s for the first byte might be because I changed “self.algorithm.set_target_subkeys(self.get_target_subkeys())” to “self.algorithm.set_target_subkeys([1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15])” in order to avoid bnum being -1 in the function, however, the first byte is obviously not getting attacked anymore…