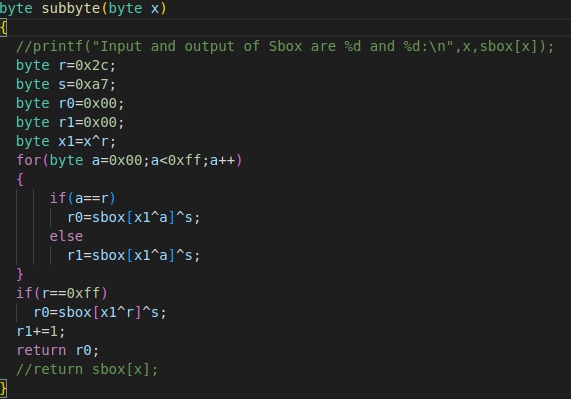
Hello, We are trying to implement first-order SBox masking in the AES encryption scheme. So, we changed the getSBoxValue function in aes.c file (path - hardware/victims/firmware/crypto/tiny-AES128-C/aes.c) to the function shown in the image. This function basically returns sbox^s(s- random number), all this extra part of the code is to avoid timing attacks. We tried retrieving the key using DPA and CPA attacks with up to 10,000 traces but the key guess was wrong. We measured the SNR value by running the measuring_snr_of_target code (path - jupyter/archive/measuring_snr.ipynb) which resulted in a value of ‘10’ while a good SNR ratio should be greater than 40 (we are using cwlite capture board). Why is the SNR value too low, is it considering the masking as noise? and Is there any other way to attack first-order masking schemes or is it just supposed to give correct key guess by increasing the number of traces in sample CPA or DPA attack codes?