Hi
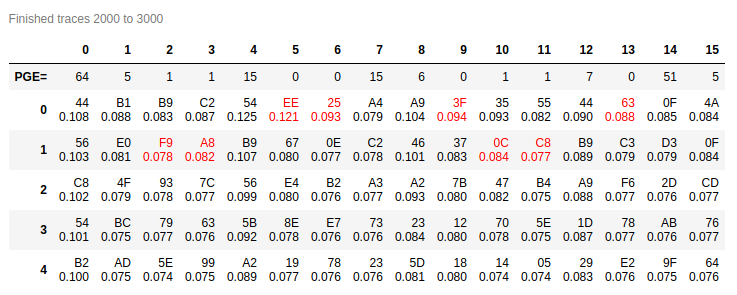
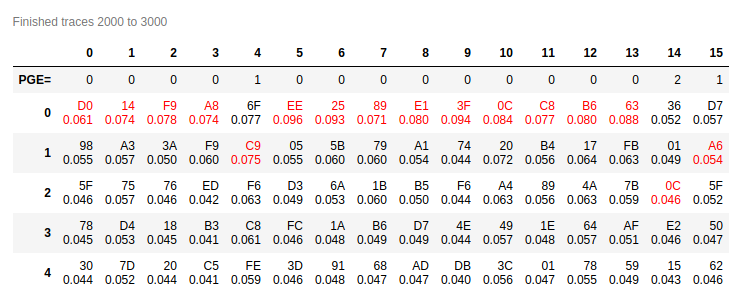
Yesterday I’ve updated my installation (develop branch) and I’ve tested it by running a Hardware Crypto Attack, but I recovered the key partially.
Things were improved with changing number of samples from 3000 to 5000. Recovered 10-12 bytes, but only 4 were with big difference in correlation.
Using diff probe didn’t help at all. Recovered 6-10 bytes, but only couple with bigger correlation.
Any ideas?
PS I tried to run this notebook on v5.1.3, but because of previous bugs I never got a key.