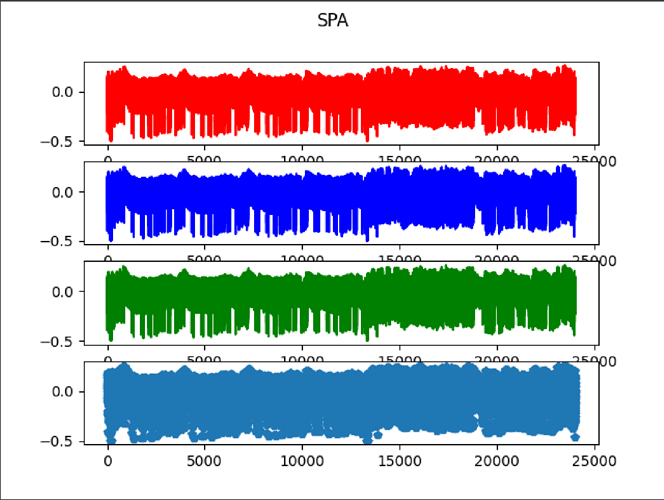
Hi everyone,
I’m trying to perform CPA and DPA on the Ascon cipher (I modified the reference implementation for it to fit on the chipwhisperer lite).
I didn’t get any good result so I decided to do some SPA to spot some of the operations.
For this I tried reducing the number of rounds of the Ascon SPN (12, 6, 3 and 1).
When I output the tag, I get a different one for each of them, probably showing that the modification are working. However, the power traces are always the same. I think I’m not measuring them the right away.
Here is the Python code I use:
f=open("traces_P12.dat", "w")
scope.adc.samples = 24000
N =100
for i in tnrange(N, desc='Capturing traces'):
scope.arm()
target.simpleserial_write('k', bytearray(key_bytearray))
target.simpleserial_wait_ack()
target.simpleserial_write('a', bytearray(nonce_bytearray[i]))
ret = scope.capture()
if ret:
print("Target timed out!")
continue
response = target.simpleserial_read('r', 16)
trace=scope.get_last_trace()
trace_array.append(trace)
for value in trace:
f.write(str(value))
f.write(",")
f.write("\n")
trace_array = np.array(trace_array)
f.close()
And here are the important functions of the C code I use:
uint8_t ascon_encrypt_own(uint8_t* n, uint8_t len)
{
// Load nonce here
for (int i=0;i<nonce_array_size;i++){
nonce[i]=n[i];
}
trigger_high();
crypto_aead_encrypt(tag, &tag_array_size,
NULL, 0,
NULL, 0,
NULL, nonce,
key);
trigger_low();
simpleserial_put('r', 16, tag);
return 0;
}
int main(void)
{
platform_init();
init_uart();
trigger_setup();
simpleserial_init();
#if SS_VER != SS_VER_2_0
simpleserial_addcmd('k', 16, get_key);
simpleserial_addcmd('a', 16, ascon_encrypt_own);
simpleserial_addcmd('x', 0, reset);
#endif
while(1)
simpleserial_get();
}
Is there somthing wrong in the way I measure the traces ?
Thanks in advance