Hi.
I am working with the victim board based on the STM32F415RGT6 MCU and I noticed interesting things.
-
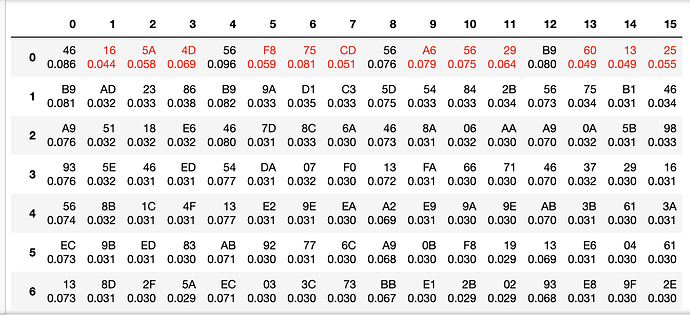
0, 4, 8, 12 positions in the AES key in most cases cannot be guessed regardless of number of collected traces. But in some cases, the key is completely recovered. What is the reason of such behavior? I use the key 11 11 11 … 11 11 11
-
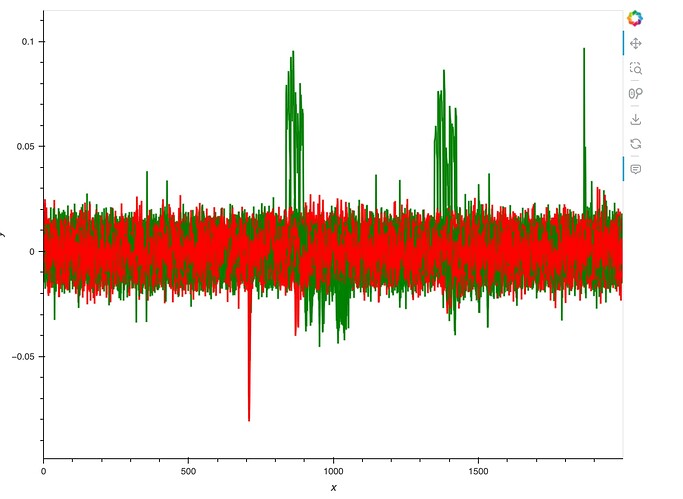
The correlation plot has two sets of high correlations which refers to the guessed key. But only first set is valid. What is the second set?
Hi,
What sort of attack are you using?
This is a Hamming distance attack against the last round of AES-128.
Any thoughts? This can be reproduced in “SOLN_Lab 2_2 - CPA on Hardware AES Implementation”
This might have something to do with using all 11’s as a key. Generally this attack is pretty reliable on this hardware. You also might want to try taking only the general area where you see the red spike as it’s possible the latter part of the power trace is throwing off your results.
Alex
This is what I found from the lab
Interestingly, you should see that the attack has worked fairly well for most of the bytes. All of them, in fact, except bytes 0, 4, 8, and 12. Looking the correlation plot, you should see two large spikes instead of one like you might expect. Try focusing the attack on either one of these points by adjusting `start=` and `end=` when making the `cw_container` and try answering the following questions:
* Which spike was our expected leakage actually at (last round state diff)?
* How might you be able to tell that the attack failed for certain bytes at the incorrect leakage point?
* Why might this other spike be occuring?
So, on your side, someone also faced with this.
Any key gives the same result regardless of the key.