Hello,
I’m wondering if someone could tell me if I’m understanding the following correctly and correct me if I’m wrong. I’m under the impression that for the AES S-box leakage model, you can calculate the SNR related to the output of the S-box for the 16 different bytes and look at the peak in order to figure out where to zoom in on the collected power traces before training a machine learning / deep learning model that’s intended to predict a given S-box output byte given a zoomed in trace. Is there a flaw in this thinking?
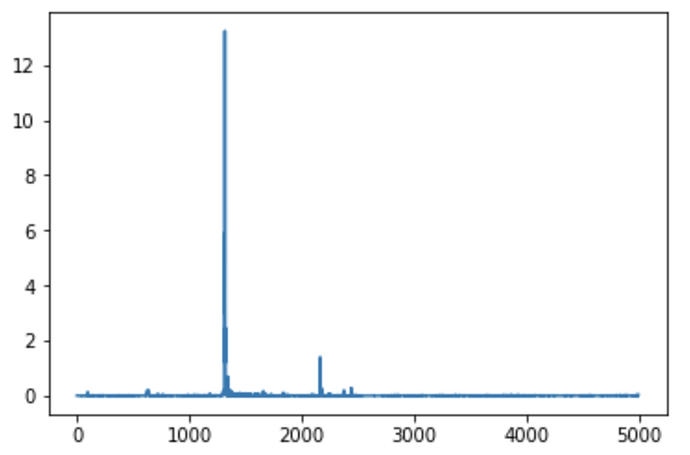
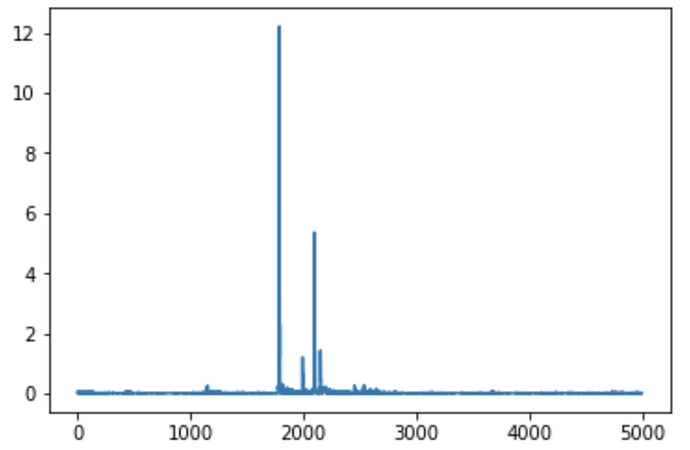
The below image is a plot of the SNR for byte 0 (with TINYAES128C loaded onto the STM32F3), but what’s interesting to me is that the index at the peak locations for the next 15 bytes doesn’t increase in ascending order by byte number. The index at the peak seems to jump back every 4 bytes. Does this mean bytes 0, 4, 8, and 12 (aka the first column in the state matrix) are substituted first, rather than going in ascending order of byte number? Maybe this is an obvious thing, but I’m fairly new to AES, so if someone could clarify this I’d really appreciate it.
Also, the SNR plot for certain bytes has additional significant peaks. Could someone explain the reason for this?
Thank you,
Jack