Hello everyone,
I am a student who has just started learning about side-channel attacks. Recently, I received the CW-Lite and CW305, and I tried to break AES with good results. However, when I used the SCA204 course to attack ECC, I encountered some problems and would appreciate any answers.
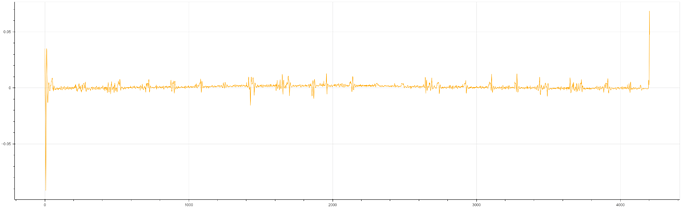
When I used one trace to differentiate between zero and one, I observed several peaks(as shown in the figure below), which were consistent with the results of the provided pre-recorded traces.
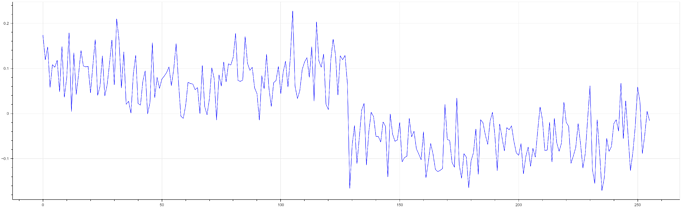
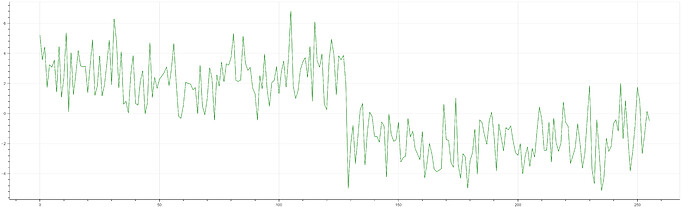
When I further captured 30 traces to distinguish k bits that are ones from k bits that are zeros, I found that increasing the number of traces did not result in a “smoother" output. In the figure below, the blue line represents the result using just one trace, while the green line uses 30 traces. The lines are almost identical, which prevented me from successfully recovering the key in subsequent experiments.
Additionally, I found some issues in the SCA204 part 1 tutorial while using CW-Lite and CW305:
- In the
get_tracesfunction ofCW305_ECC_setup.ipynb, thewavevariable is not defined before it is used; - The length of the wave collected using CW-Lite exceeds 1130000, causing the
get_sumsfunction inCW305_ECC_part1.ipynbto output incorrect results.
I have fixed the above issues in Jupyter, but it still does not work properly. I look forward to your response.
Li