Hello, im working with Chipwhisperer Lite, CW303 target, V4 and i have some questions:
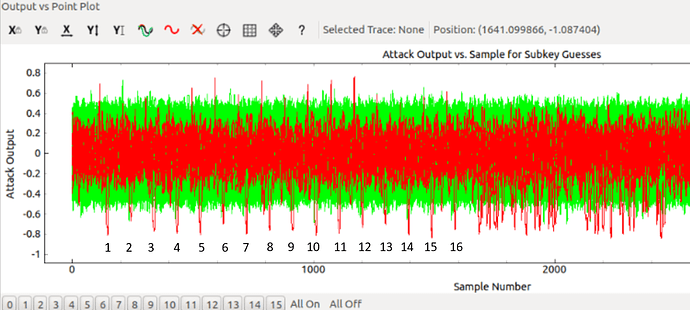
I was doing the Tutorial B5 Breaking AES (Straightforward) and looking at the points of higher correlation and i find out that they are distributed in the first 1600 points of my 3000 point trace, as we can see in the image.
That means that in the trace that im watching is only the first round of AES?
If i want to attack for example other point of the algorithm (not the first subbyte call) i should pick more traces or the aes example just compute the first round?
If it computes the complete AES how many points i should capture?
Hi Nick,
The AES example should go through all 10 rounds, unless you haven’t reprogrammed it (IIRC the CW303 ships with an incomplete version of AES). You’ll need to capture longer traces or change your offset to attack elsewhere. You can find the length of traces you need to capture from scope.adc.trig_count.
If you’re looking to try attacking other spots in software AES, I’d suggest the input to the final SBox, since that allows you to launch an attack with the ciphertext instead of the plaintext. I’m not sure what it’s called in CW4/earlier, but in CW5 the correct leakage model is LastroundHW.
Alex
Thanks for the quick answer! I have another question.
I was working in a algorithm countermeasure, so i modify the aes.c of tiny-AES128-c directory. I know that my countermeasure give the correct answer (i mean it return the correct ciphertext), but when i put it on CW303, the output isnt right.
.
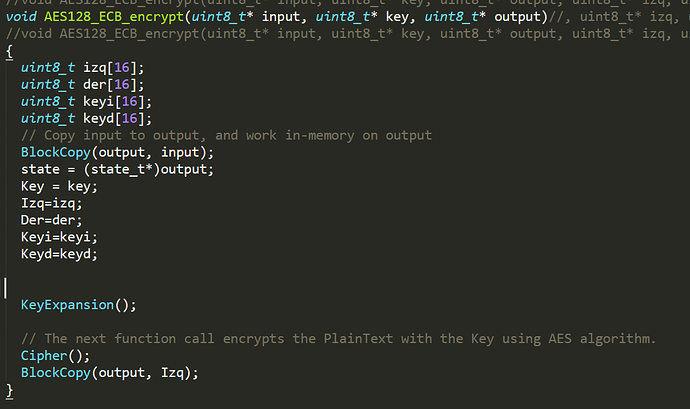
As we can see in the image the plaintext is copied in output.
Here is the part of the code that i think is guilty of this, but im not sure. “Izq” is my ciphertext (its an array[16]).
higher in the aes.c code i found 2 other functions that can be related with this error (void AES128_ECB_indp_setkey(uint8_t* key) and AES128_ECB_indp_crypto(uint8_t* input)), but i dont know which of these are invoked in the chipwhisperer implementation. I’m not sure if I’m implying, i need to make that somehow “Izq” = output. But i dont know which function use the chipwhisperer for do the cipher or why it isnt working.
Hi Nick,
AES_ECB_indep_crypto() is the function called by ChipWhisperer.
Alex
I have the feeling that the cipher is running well, because the waveform of the trace changed and the old function cipher() contains only the countermeasure. But something is wrong when i try to copy the result on the output.
You have the arguments for BlockCopy() swapped as well, assuming you’re trying to copy output into Izq and not the other way around
Thanks very much! But, in the function
void AES128_ECB_indp_crypto(uint8_t* input)
{
state = (state_t*)input;
Cipher();
}
I dont understand where the Cipher() result is copied in the output.
state is a global pointer variable that is being reassigned to input.
Im trying to make my output = Izq (Izq is the ciphertext), but i still dont understand how using void AES128_ECB_indp_crypto(uint8_t* input) its the output of the cipher = to output, or where did i set the key.
input is both the input and output of the function, so you’ll want to move lzq into input.
Ok, i did that. But now somehow Izq dont have the correct answer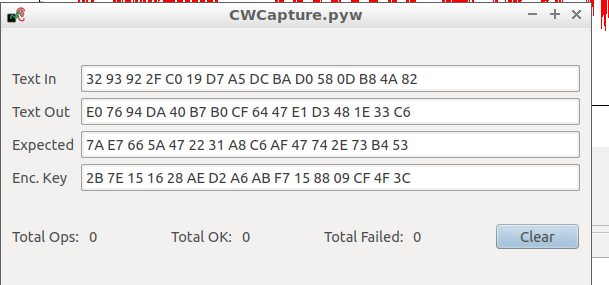 .
.
Maybe its because in the countermeasure a function called keyexpansion2() is used and not keyexpansion(). Maybe should I change it somewhere?
Now im sure that my problem is related with the Key, somehow the new function Keyexpansion2() is working with the plaintext as initial key and not with the secret key. How is the initial key seted?
I don know why, but plaintext is seted as plaintext and secret key. So if i choose same secretkey and plaintext the cipher work well.
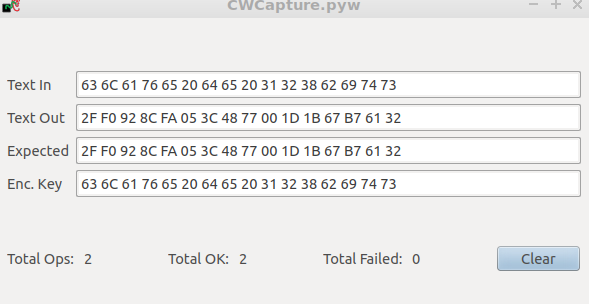
Any idea why this happend?
Fixed, thank for the help!
1 Like
 .
.