I am still struggling to attack the rounds other than the first on plain DES.
I’ve made significant changes to the DES model to output the sbox values from the required round. I am fairly confident that the sbox values are correct having stared at a load of print() messages but the attacks fail.
I am also fairly certain that the trace I am attacking is from the second round but as it’s not working something isn’t right.
The way I am doing it is thus:
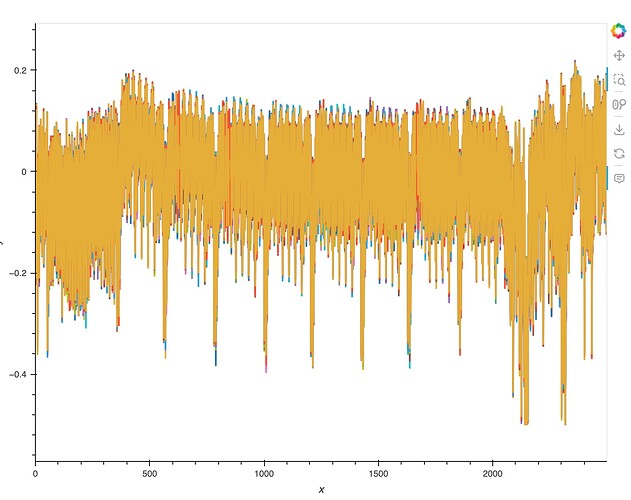
Capturing 100 traces from the XMEGA target. Round 1 comes in at offset 73500 and round 2 at offset 131500, so I am capturing 5000 samples at offset 131500. The 8 sboxes are clearly seen between samples 400 and ~2200.
Running the attack using this code:
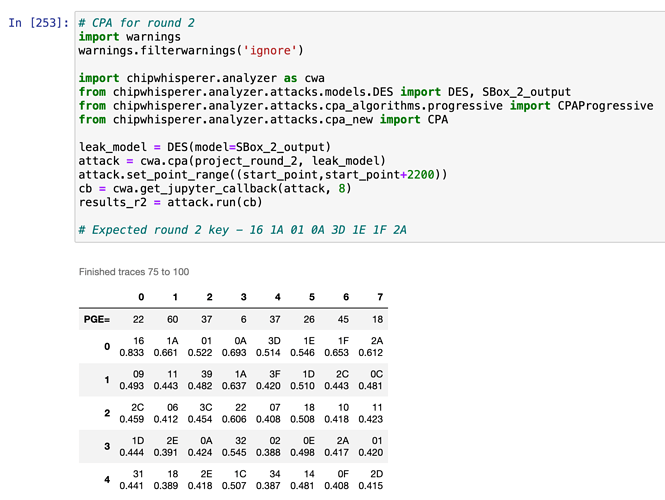
import chipwhisperer.analyzer as cwa
from chipwhisperer.analyzer.attacks.models.DES import DES, SBox_output
from chipwhisperer.analyzer.attacks.cpa_algorithms.progressive import CPAProgressive
from chipwhisperer.analyzer.attacks.cpa_new import CPA
attack_round = 2
leak_model = DES(model=SBox_output(attack_round=attack_round),attack_round=attack_round)
attack = cwa.cpa(resync_analyzer, leak_model)
attack.set_target_subkeys([0, 1, 2, 3, 4, 5, 6, 7])
attack.set_trace_source = attack.project.trace_manager()
attack.set_trace_start(0)
attack.set_traces_per_attack(-1)
attack.set_iterations(1)
attack.set_reporting_interval(10)
attack.set_point_range((300,2500))
cb = cwa.get_jupyter_callback(attack, 8)
results = attack.run(cb)
The attack_round tells the model how many rounds to run within the DES routine before exiting, returning the sbox output values for a given byte number sent by the CPA module.
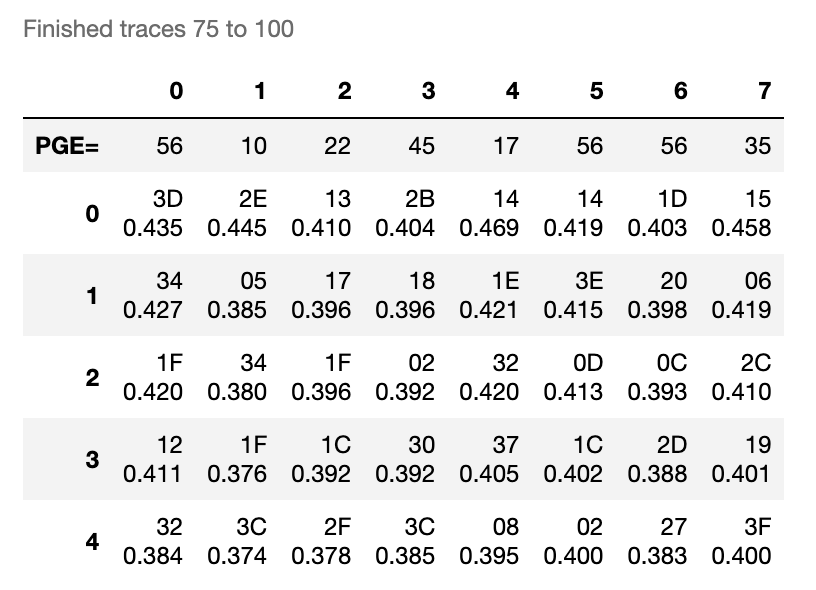
As I am attacking the second round key, I am expecting key 16 1A 01 0A 3D 1E 1F 2A to pop up (round 0 key is 2B 7E 15 16 28 AE D2 A6)
But I am getting no outliers from the attack…
If I target traces from round 1 and set attack_round to 1, it works great.
So, I am either targeting the wrong trace or there’s something wrong with the model.
Halp!
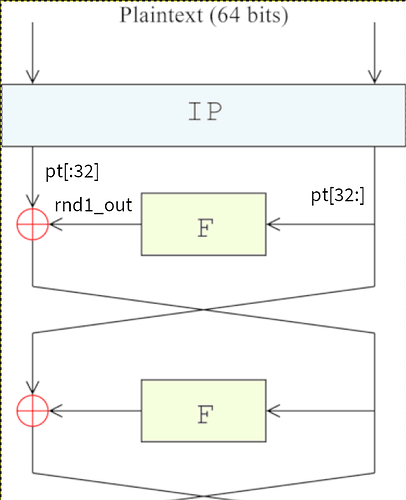
Edit: just a thought… Do I need to know the input into round 2 before getting its output? I wouldn’t have thought so…