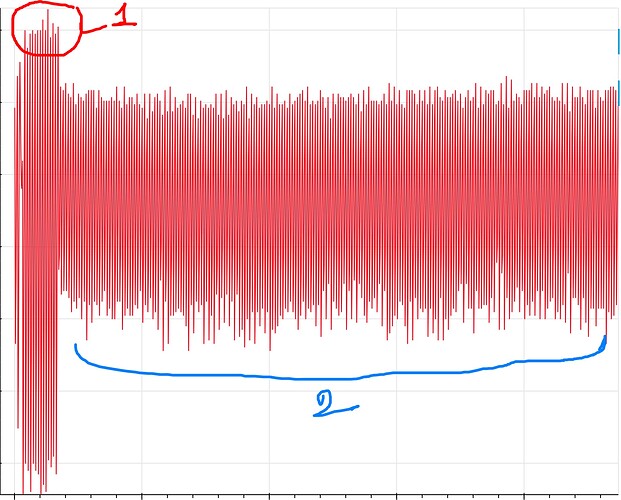
I am trying CPA attack on AES 256 and using CW305 FPGA target board. For AES 256,I am using the provided code from chipwhisperer. The power trace for one encryption appears as below:
In the above probing:
- target frequency = 5MHz
- scope.adc.sample = 1000
My questions are:
-
In the above waveform, where is the 14 rounds of operations, in zone1(red) or zone2(blue)? I count 14 spikes in red marked zone 1.
-
I tried to use the default CPA attack provided in the notebook of aes128 demo. I am using my custom key as follows:
knownkey = [0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11,
0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11, 0x11]
key = bytes(knownkey)
and text as usual from _, text = ktp.next().
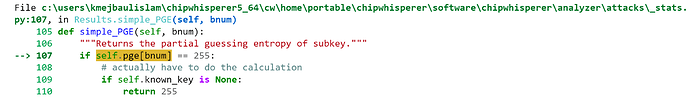
After probing some traces and saving as project, when I run the attack using attack_results = attack.run(cb), it shows error IndexError: list index out of range like following:
Knowing the issue is the key, how can I make it work for 256bit keys? Is there any default options in chipwhisperer analyzer for 256 bit keys or I need to use custom CPA tool?
- In the definition of ktp, I did not find a way to generate 256 bit keys. If there is a way doing to using ktp, please let me know.